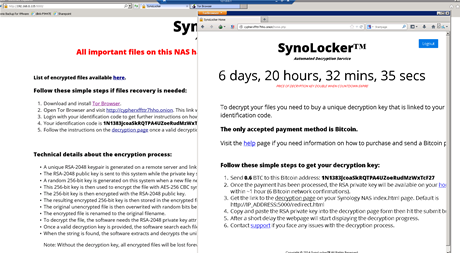
Extortionists have encrypted data on more than 10,000 patients and various research projects at a Hong Kong hospital using a flaw in network attached storage maker Synology's software, and are demanding a ransom to return access.

The South China Morning Post reported that the Centre for Liver Health and Institute of Digestive Disease at the Prince of Wales Hospital had been hit by blackmailers who are demanding 0.6 Bitcoin (approximately A$372 presently) to decrypt the scrambled files.
Hong Police said the extortionists used the SynoLocker ransomware to encrypt the files on two servers.
A spokeswoman for the faculty said that while staff could no longer access the patient data as well as some research and teaching materials, it did not appear that information had been stolen.
The faculty has disconnected the servers from the network and has notified the Hong Kong privacy commissioner of the attack.
Synology has acknowledged the vulnerabilities in its DiskStation Manager software that the SynoLocker extortionists are exploiting, telling users to upgrade to the latest 5.0 version that has patched them.
"Based on our current observations, this issue only affects Synology NAS servers running some older versions of DSM (DSM 4.3-3810 or earlier), by exploiting a security vulnerability that was fixed and patched in December, 2013. At present, we have not observed this vulnerability in DSM 5.0."
- Synology statement 4 August 2014
Update 10:14am: A spokesperson for Synology told iTnews that SynoLocker encrypts user files and lock people out who don’t pay the extortion fee.
“So far, we have seen a number of people say they’ve paid the ransom, on Twitter,” the spokesperson said.
“The incentive [to pay the ransom] is equally appalling, apparently, if you don’t within a certain number of days, the ransom doubles,” the spokesperson added.
He reiterated that the vulnerability is preventable with software updates.
Users around the world are currently reporting SynoLocker attacks but it isn't clear if there is a way to decrypt the files without paying the ransom.
Synology suggests that victims who have had their files encrypted contact them on security@synology.com.



_(37).jpg&h=140&w=231&c=1&s=0)

_(33).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



