Notorious hacker group Team GhostShell has posted a trove of a claimed 36 million accounts and database records from vulnerable and misconfigured MongoDB installations.
As with prior dumps, the hacktivists posted a brief message on Pastebin with links to the file locker sites where they had uploaded the approximately 6GB archive with the purloined account details.
Team GhostShell said it had conducted the hacks to raise awareness of poorly configured MongoDB database instances on the internet that allow access without username and password credentials.
"I am leaking more than 36 million accounts/records of internal data from these types of networks to raise awareness about what happens when you decide not to even add a username/password as root or check for open ports, let alone encrypt the data," the hackers wrote.
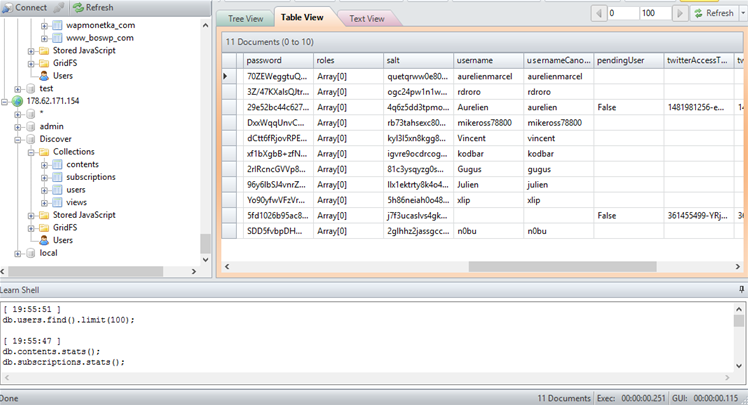
The databases contain personally identifiable information such as email and physical addresses, phone numbers, and other sensitive data.
The archive also contains user names and passwords, most of which appear to be encrypted with salt to make decryption of the credentials harder..
Last year, the operator of the Shodan vulnerability scanning website, John Matherly, warned that nearly 30,000 MongoDB instances were running old and insecure versions of the open source database.
This meant that almost 600 terabytes of data was left exposed to the internet, Matherly said.
Alleged GhostShell hacker still free
Team GhostShell hit the limelight in 2012, when the group leaked 1.6 million accounts and database records for 37 well-known United States defence and aerospace contractor companies, along with the European Space Agency and the National Aeronautics and Space Administration (NASA).
That same year the hackers also dumped a large amount of data obtained from Russian companies and government organisations to protest against corruption and poor living conditions.
In March this year, a 24-year-old Romanian man claimed to be the founder of Team GhostShell, providing login details for the hacking group's Twitter and Pastebin accounts, along with passport photos and other documentation.
Whether or not the Romanian man, who took responsibility for 99 percent of the hacks, is Team GhostShell remains to be proven. He has not been arrested by Romanian police.



_(33).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



