The chief technology officer of a Sydney-based penetration testing firm has warned of an increasing obsolescence of stock shell codes used in penetration testing and hacking, calling on infosec professionals to begin writing their own variants.
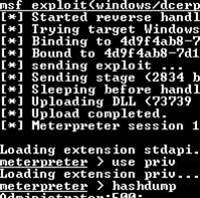
Pure Hacking's Ty Miller told SC that stock shell codes, such as that used in the popular Metasploit Framework, had become less suitable for penetration attempts, often hitting firewalls and authentication systems.
They were designed to exploit mail and other servers but most targets had since moved to client software.
“These days we’re attacking software like Adobe, trying to break out of it,” Miller told SC. “Your custom shell will do things like tunnel out through DNS, or over FTP, without unintentionally hitting firewalls.”
Custom-built shell codes were of greater value, he said, as they outlived the typical three-month half-life of an individual exploit.
Shell code is a payload of software exploits that operates from a command shell. It gives more capability to an attacker and remains effective longer than exploits alone, which might be patched quickly.
Shell code could be reused in most exploits and remained viable for up to a decade.
Though most infosec professionals were used to running stock shell code, Miller said custom code was far more effective and capable.
Miller has focused in past years on building custom shell code rather than exploits. He had integrated a number of the applications with Metasploit to take advantage of the frameworks’ 600-plus exploits.
He will run a two-day training course on how to build custom shell code and integrate with Metasploit at the BlackHat conference in Las Vegas next week.
It will examine all types of shell code, Miller said, including dynamic shell code, portbind, connectback, egghunt, and command execution.



.png&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



