Security researchers have unearthed a sophisticated campaign that targets consumer-grade routers from multiple manufacturers in Europe and North America.
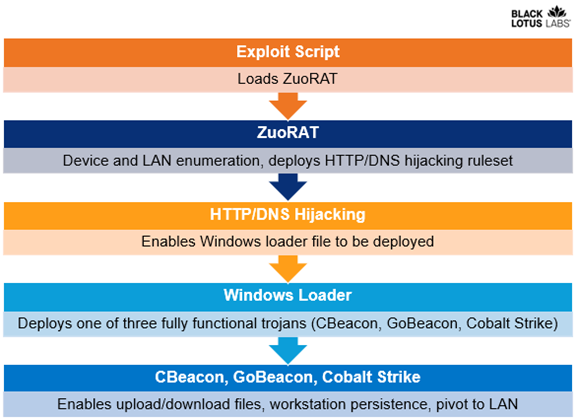
The researchers at security vendor Lumen's Black Lotus Labs spotted the ZuoRAT multi-stage remote access tool hijacking small business and residential routers from brands such as Cisco, ASUS, DrayTek and Netgear.
They note that SOHO [small office/home office] devices are rarely monitored or patched.
Black Lotus Labs named the first stage of the malware ZuoRAT after the asdf.a filename, which points to left-handed typing by the malware author, and says it's been used since at least 2020.
The ZuoRAT adfs.a file runs on routers with MIPS processors, and can enumerate hosts and internal networks.
It can also perform packet capture, man-in-the-middle hijacking of domain name system lookups, and web traffic re-routing.
After a router has been hijacked, a loader for Windows computers can deploy one of three Trojans: CBeacon, GoBeacon or Cobalt Strike.
The threat actors have tried to hide their command and control infrastructure, including traffic redirection, which suggests a nation-state adversary, Black Lotus Labs said.
"While compromising SOHO routers as an access vector to gain access to an adjacent LAN is not a novel technique, it has seldom been reported.
Similarly, reports of person-in-the-middle style attacks, such as DNS and HTTP hijacking, are even rarer and a mark of a complex and targeted operation.
"Combining of these two techniques demonstrated a high level of sophistication by a threat actor," the reseachers wrote.
Black Lotus Labs found Chinese characters in malware samples, and the Windows RATs interacted with C2 infrastructure hosted on Alibaba Yuque and Tencent networks in China.
Due to the limited monitoring capabilities in the compromised routers, Black Lotus Labs said it has only a narrow view of the campaign.
The good news for users is that ZuoRAT doesn't persist through reboots, so Black Lotus Labs said users should regularly reboot their routers.
They should also apply vendor patches when available, and businesses should consider secure access service edge solutions to enhance their security posture.


_(23).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)

_(28).jpg&h=140&w=231&c=1&s=0)



_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



