Security researchers at Resecurity have detailed a new phishing-as-a-service kit, EvilProxy, that provides an easy to use interface to attack users with accounts for major online brands, and the ability to bypass multifactor authentication (MFA).
Resecurity
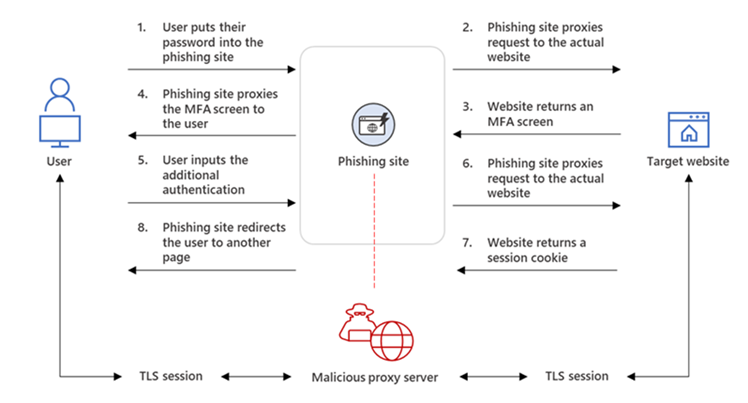
Reverse proxies to attack multifactor authentication, such as Modlishka, have been available for several years, but EvilProxy makes it it possible to easily create and deliver advanced phishing links through a graphical user interface, Resecurity said.
EvilProxy sits between a victim and the real site the user is trying to connect to, capturing their valid session cookies, to bypass the need to authenticate with user names, passwords, and / or two-factor authentication tokens, the security vendor explained.
This includes accounts that have MFA enabled with short messaging text service, or application tokens.
Accounts with major brands such as Apple, Facebook, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, Twitter, Yahoo and Yandex can be attacked with EvilProxy.
Available since May this year, Resecurity said EvilProxy costs US$400 a month to rent.
CyberCX executive director of security testing and assurance Adam Boileau explained to iTnews that EvilProxy cannot bypass hardware key authentication.
"U2F, FIDO, and WebAuthn are cryptographically bound to the site they are authenticating to - there is some public/private key stuff and basically the challenge that the hardware key answers is signed, such that only the real site can process the response," Boileau said.
"The responsibility of understanding who you're authenticating to is taken out of human hands," he added.
Boileau said every other MFA scheme such as one-time passwords and push notifications require humans to be involved in the above choice.


_(20).jpg&h=140&w=231&c=1&s=0)








 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



