Microsoft's open source NLWeb framework for delivering AI-driven agentic web applications shipped with an easy to exploit path traversal vulnerability that revealed the context of sensitive system files and allowed the theft of authentication keys.
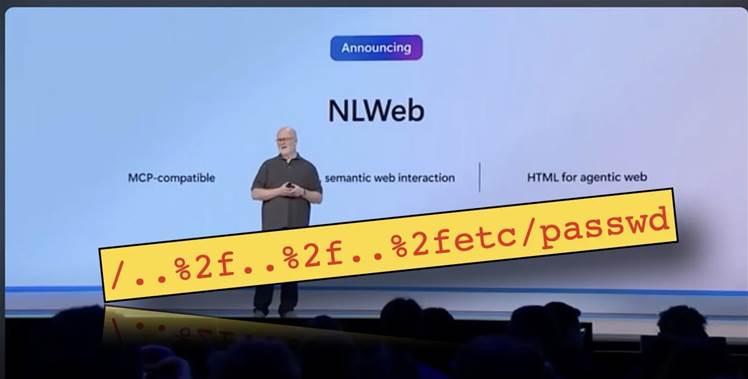
Security researcher Aonan Guan discovered the vulnerability after recognising a Python programming language function, os.path.normpath, used for sanitisation of user input, in the NLWeb's open-source code.
Testing confirmed that the function allows users to move out of their intended directory, by using ../ sequences.
Guan set up a test server, sent a command with URL-encoded traversal sequences, and was able to access system files.
The command displayed the contents of the test system's password file, but could be used to access others as well, including application programming interface keys for AI models, and server configuration, Guan said.
A consequence of being able to access the API keys for large language models (LLMs) is that attackers can "steal" an agent's ability to think reason and act.
This, Guan said, has the potential to lead to massive financial loss from API abuse, or the creation of a malicious clone of the agent.
Path traversal could also force AI agents to read local files, and even maliciously crafted documents, which could poison the system's retrieval augmented generation (RAG), which could create incorrect or biased information.
NLWeb (Natural Language Web) was launched in May this year, with Microsoft describing the software as an open project "that aims to make it simple to create a rich, natural language interface for websites using the model of their choice and their own data".
It is also a model context protocol server, that follows the standard developed by Anthropic for connecting AI assistants to external data sources.
After reporting the flaw to Microsoft on May 28, the company committed a patch to the NLWeb public GitHub repository on June 30.
Guan advised organisations trying out NLWeb to update their deployments immediately, and to implement web application firewall/reverse proxy rules to blog and log any URL requests that contain encoded traversal sequences such as ..%2f.
Users should also avoid exposing the NLWeb application server directly to the public Internet and instead put it behind a hardened reverse proxy with firewall rules to restrict access, Guan said.


_(28).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)






 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



