Real estate listings business REA Group has released an updated version of its realestate.com.au Android application to fix a vulnerability that sent login credentials over an unencrypted connection.
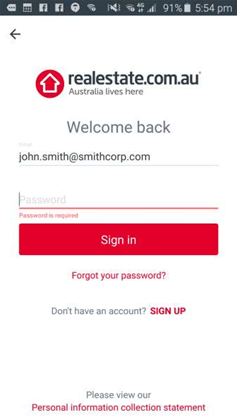
The business was alerted to the vulnerability by security researcher Troy Hunt last Sunday, and responded within seven minutes, Hunt said.
He had discovered that when entering login details (username and password) on the realestate Android app, the first request to /login/session was sent over HTTP - an unencrypted connection - to REA's servers.
The request later redirects to a secure connection, Hunt found, but the damage was done in the initial unsecure connection.
The same issue did not exist on realestate's iOS application, Hunt said, which sends the credentials over the encrypted HTTPS protocol from the beginning.
He said the error was a "dead easy mistake to make".
"There is literally one character missing in someone’s config file for the Android app and that makes the difference between having a strongly encrypted connection from the device to the server versus having zero encryption at all on the first request," Hunt wrote.
"The fact that the login page simply redirects the insecure request then hides the misconfiguration, but it’s an understandable pattern because that’s what we normally do when we want to enforce HTTPS on a website – we 301 to the secure scheme if it’s accessed over HTTP."
Hunt praised REA Group for its fast reaction, including the issuance of an updated version of the Android app in the Google Play store the next day after being notified.
"An issue like this is so easy to slip through into production, how it’s handled is the real test of the organisation IMHO," Hunt wrote.
REA Group thanked Hunt for his responsible disclosure and for giving it the time to confirm, patch, test and release the fix.
"While we believe we responded in a timely fashion to this alert, the fact is the vulnerability existed in the first place," REA infosec and risk employees Aaron Wigley and Dick Ward wrote.
"This is where our organisational culture within REA helps us – a key component of how we work is that we try and make sure we learn from our mistakes.
"Since we were made aware of the issue, we have been asking ourselves deeper questions (beyond the obvious questions around how this technical mistake was made). This is a practice we’ll continue to ensure our IT security is at its best."



_(36).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



