A joint strike by police in the Netherlands, Germany, the United States, United Kingdom, France, Lithuania, Canada and Ukraine appears to have taken down the infrastructure for the notorious Emotet malware.
Coordinated by Europol, law enforcement in the above countries say they have now taken control of the infrastructure for what police termed the "world's most dangerous malware".
Police have taken control over several hundred servers around the world, Europol said.
Infected machines are now being redirected towards the law enforcement controlled infrastructure.
Ukraine Police posted a video of premises in the country being raided, with arrests made and large amounts of cash, gold bars and IT equipment seized.
The first deputy officer of Ukraine's national cyber police department, Serhiy Kropyva, estimated the Emotet operators had caused US$2.5 billion in losses due to their attacks on private and public institutions in Europe and the United States.
Kropyva said the Emotet criminals face up to 12 years in prison.
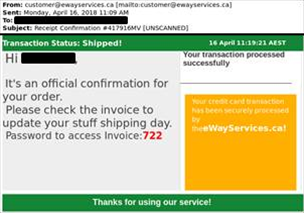
Starting off as an information stealing banking trojan in 2014, Emotet evolved into a loader for other malware like Trickbot and Ryuk, police said.
Other criminals have been able to hire Emotet to install ransomware and info-stealers on victims' computers.
The police operation appears to have been successful.
Security company Team Cymru which has been tracking Emotet activity noted that amount of malware controllers had dropped from over 100 to zero in very short timeframe.
— Cryptolaemus (@Cryptolaemus1) January 27, 2021
The Emotet operators ran three separate botnets, Team Cymru said.
Team Cymru said the drop in top level controllers for Emotet showed that the initial takeover of the malware infrastructure was a profound success.
US authorities estimate that the complex and highly resilient Emotet malware - which spreads through malicious download links, Microsoft Word document macros, and Adobe Portable Document Format (PDF) files sent via emails - cost US$1 million per incident for government agencies to remediate.
Europol advised that the Dutch police has set up a database with seized information from the Emotet botnet.
Users can check if their email is in the database; if it is, it means their computers are likely to be infected with Emotet.
Update, 7.58am: Dutch police said that two out of the three main Emotet control servers were located in the Netherlands.
As part of “Operation Ladybird”, the servers now under Dutch police control will send out a software update for Emotet, which will deactivate the malware on infected systems.
A security researcher going by the moniker Milkream noted that the payload contains code to delete Emotet, by March 25 this year.
The date chosen is to give experts time to analyse existing infections, to see what other malware has been deployed by Emotet, Dutch police said.


_(36).jpg&h=140&w=231&c=1&s=0)


_(33).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



