A joint operation between international law enforcement agencies, Microsoft and security vendor ESET has dismantled the Andromeda botnet responsible for infecting millions of computers around the world.
The botnet take-down was co-ordinated by the FBI in cooperation with Europol and German police.
Andromeda, which is also known as Gamarue, was used to distribute other malware and has been active since September 2011 at least, ESET said. It's been linked with 80 other malware familes and was used for the worldwide Avalanche botnet that was taken down in December last year.
Europol today said one suspect has been arrested in Belarus.
Belarus state media said the 37-year-old man earnt US$500 per sale of Andromeda, and US$10 per update for the malware. The total of revenues brought in by the malware business is yet to be ascertained.
The man's hard drives, other data storage, and digital wallets have been seized by Belarus police and are being investigated.
Some 1500 domains associated with Andromeda were sinkholed, a technique used to prevent computers infected with the malware from reaching command and control servers by redirecting traffic to servers controlled by security vendors.
Microsoft said in 48 hours of sinkholing, around two million unique IP addresses of infected machines across 223 countries were recorded.
Over half of the total number of computers running the Andromeda malware remain infected. The sinkholing will remain in place for another year globally, including in Australia.
Microsoft said its telemetry shows almost 1.1 million computers a month were infected by Andromeda this year.
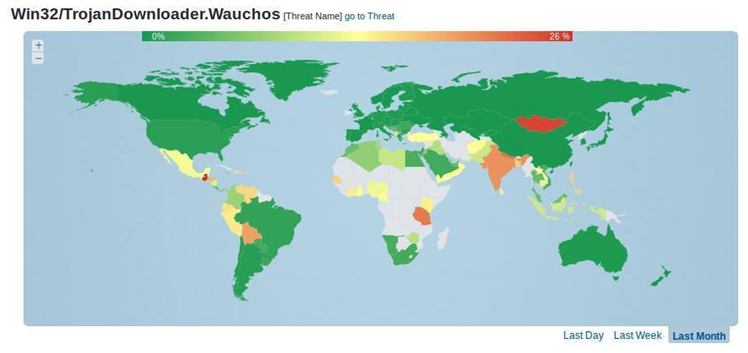
ESET's analysis of Andromeda/Gamarue, which the security vendor calls Wauchos, noted it was used to steal credentials and download and install further malware on infected computers.
This means Andromeda-infected computers are likely to harbour other malware such as the Neutrino distributed denial of service attack bot, as well as the Kelihos and Lethic spamware.
Andromeda is modular malware and its functionality can be expanded with plug-ins such as keyloggers and form grabbers to capture and exfiltrate users' personal information, ESET said.
The malware has spread worldwide through social media, instant messaging, spam, and removable hard drives.
It would detect if a target system's keyboard layout was set to Russian, Ukrainian, Belarus or Kazakh languages - if so, Andromeda would exit without doing anything malicious.
This tactic, ESET speculated, "is presumably intended to ensure that the bad actors avoid prosecution in those countries".



_(28).jpg&h=140&w=231&c=1&s=0)

_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



