Phishers have come up with a new technique to trick users by simulating browser windows with the browser itself in order to spoof legitimate domains, which is hard for victims to detect.
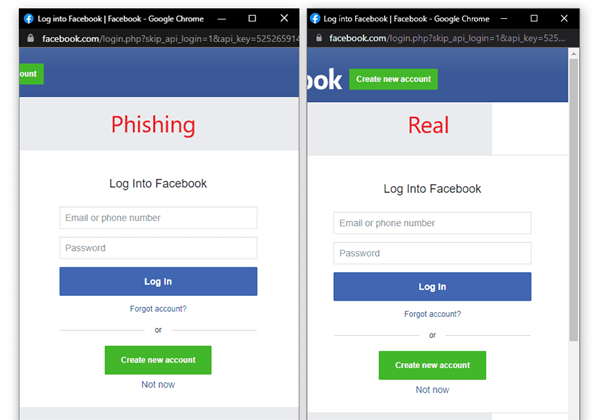
A security researcher using the moniker mr.d0x has documented how phishers create bogus pop-up windows for Google, Microsoft and Apple websites which look almost exactly the same as the legitimate ones for authenticating users.
It is difficult for users to work out that they're on fake sites, mr.d0x wrote.
"... once landed on the attacker-owned website, the user will be at ease as they type their credentials away on what appears to be the legitimate website (because the trustworthy URL says so)," mr.d0x wrote.
Oh, this is good.
— Will Dormann (@wdormann) March 16, 2022
Think you're typing into a pop-up window? Make sure that you try to drag it OUTSIDE OF the content area of the page first.
Surely normal human beings do this. https://t.co/MLJzvUFkLW pic.twitter.com/zB1QbjpgKq
Meanwhile, security researchers at Trustwave Spiderlabs say some phishers have started using landing pages that are automatically customised to look more authentic.
Spiderlabs tested a phishing message with links that pointed to common email providers such as Google Gmail and Microsoft's Outlook.com, and found that the landing page elements changed accordingly.
The security researchers noticed that at least four elements were changed to match the phishing links, using Javascript.
These include the page background, a blurred logo, the title tab and the capltalised text of the domain, from the email provider, which all changed to trick victims into thinking they were on an authentic site.
Spiderlabs said "chameleon" sites with customised page templates are often used by malware authors, and also used to steal user credentials.


_(23).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



