NAB has replaced the internal platform it uses to orchestrate its response to the detection of phishing sites targeting the bank’s customers.

Senior cyber security specialist John Murphy described it as one of the early “big wins” from NAB’s deployment of Splunk’s Phantom security automation and orchestration (SOAR) software.
Detections of suspicious sites - from customer reports via SMS or email, and “a number of other” avenues that NAB declined to discuss - are fed into a set of Phantom playbooks that handle various aspects of the incident response.
In incident response, playbooks (and runbooks) are lists of triage, investigation and remediation steps to take once an incident is detected.
These can be automated using SOAR suites, which often come with phishing playbooks out-of-the-box, as is the case with Phantom.
In NAB’s case, Murphy said the bank is using “15, maybe 20 playbooks” in Phantom to respond to phishing threats.
“These [threats] are websites that are set up with our brand intending to steal customers' money basically, so our job is to detect these sites as quickly as possible and get taken down immediately,” Murphy told Splunk’s .conf19 in the United States last month.
The playbooks handle steps such as “confirmation and rejection … that analysts can use to provide feedback [to the customer] as to whether the alert is phishing or isn't”, as well as initial checks to work out if the phishing campaign is new or further evidence of one already under investigation.
Supplementary playbooks can be used to “grab a screenshot of the suspected site” or to access the site’s whois information, which would identify the host and potentially the site owner.
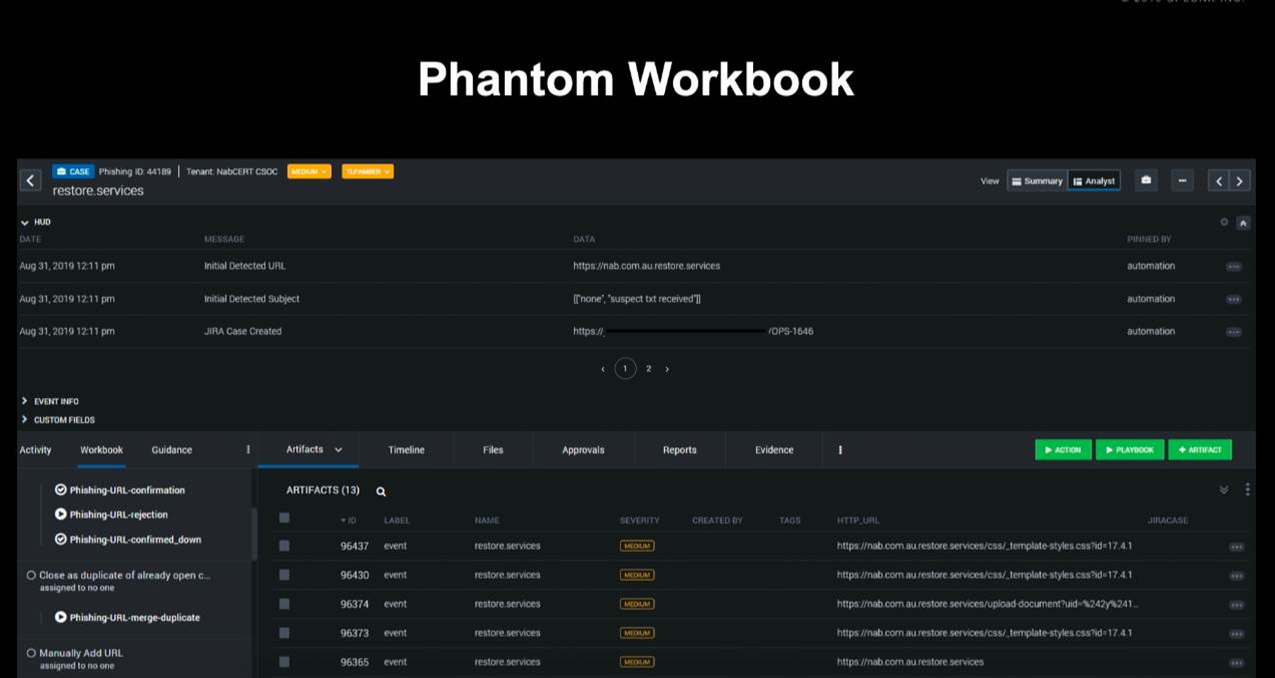
Murphy provided an example “workbook” - or screen - that is displayed to a security analyst.
“At the top, we have the pinned information, which is the detected URL; if it came from an email it includes the subjects that we've seen, and also a link to our JIRA case [used for evidence collection],” he said.
“At the bottom, there's all the emerged artifacts from all of our different detections. And because we have detections at different stages of the phishing lifecycle, we see a lot of URLs being grouped together in this case.
“Then, on the left hand side, we have a number of playbooks that an analyst can kick off, depending on their analysis of the suspected URL.”
The analyst could jump back and forth between JIRA and Phantom easily to investigate the URL and document their findings.
Playbook design
The number of playbooks NAB uses in its response to potential phishing site detection is likely a by-product of its learnings from having Phantom in production for the past year.
“If you're new to building playbooks and you don't know where to start - like us about a year and a half ago - here's some points that will hopefully get your head in the right direction,” lead cyber security specialist Chris Hanlen said.
“If you're trying to build full end-to-end playbooks, you might get bogged down in the detail and you might not see the forest for the trees, so to speak.
“So, our suggestion is using workbooks - or case management, in the old parlance. By splitting out the major functions or the major tasks of your playbook into manageable little sub components, it'll allow you to more rapidly develop your playbooks and hopefully realise the return on investment a bit quicker.”
Hanlen said the disadvantage of “monolithic, cumbersome playbooks” was that they could “take 20 minutes” - or presumably more - to run and process.
“Try and think about building atomic playbooks - small playbooks with a specific function, so that they will process within two or three seconds - over and done,” he advised.
“You then take parent playbooks, and you stitch together, or you call all of the different atomic or sub-playbooks, and that way you'll hopefully get to a full end-to-end playbook processing for whatever use case you're developing.”
Automating SOC ops
Hanlen said that the broader intention for adopting Phantom was to automate some of the bank’s security operations centre (SOC) activities, though he noted it was not about replacing staff.
“At the end of the day, we're trying to come to terms with all of the different events that are hitting us,” he said.
“We've got a lot of systems, which are feeding into Splunk, and generating a lot of alerts that our SOC has to deal with.
“So basically, it's about removing all of the noise so that our analysts can work on the big ticket items.”
Hanlen said that “every single alert” generated from Splunk’s enterprise security product is routed through Phantom.
“It's initially ingested into a label called Splunk - funnily enough - and this is where all of the generic event processing is performed.
“We then perform a label switch to switch the event into one of 13 lower-level response categories, and that's where the alert-specific processing is performed for the event.”
The bank noted in a slide deck that it saw “averages” of “800,000+ security events, 2000+ security alerts investigated, 600,000+ malicious/spam emails blocked, and 1000+ phishing sites taken down”, though did not clarify in what time period this occurs


_(36).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



