Rogue developers were found to have laced the world's most popular torrent client with code that foisted unwanted and potentially malicious software onto Android devices, researchers say.

Xunlei Networking Technologies admitted now fired staff had introduced functionality to the Xunlei (aka Thunder) download manager that would drop malware on Windows boxes and push heavily-obfuscated code to any connected Android device.
Xunlei was rated the most popular torrent client in a 2009 report by bittorrent site the Pirate Bay. Recent statistics do not exist, however the uTorrent client could be the most popular outside of China.
"Not only were the binaries signed with [Xunlei Networking Technologies'] certificate, but the domain kankan.com, whose subdomain is used as StatServer, corresponds to the company’s video-on-demand service. So there is little doubt about the company’s implication in the production of this piece of software," ESET researcher Joan Calvet said.
Calvet said the company said that staff in one of its divisions were responsible and have been fired.
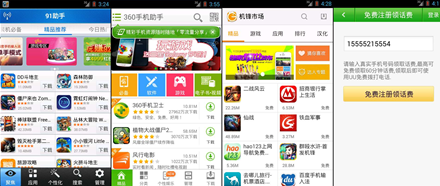
Thousands of Chinese users who downloaded the compromised Xunlei program during August and September could have had their connected devices compromised.
The malware worked according to Calvet and her team by registering a functionless Microsoft Office plugin that established persistence on user machines.
It would retrieve a series of commands from a Xunlei-run servers and download the Android Debug Bridge to locate and communicate with Android devices connected via USB. The debug bridge was part of Google's Android software development kit.
Only Android devices with debugging mode enabled could be infected. This meant that rooted devices -- those modified to run custom operating systems -- were most at risk because the mode was activated during the root process.
Seemingly innocuous Chinese-language software was then uploaded to Android devices and installed without the need to ask user permission, a feat made possible thanks to the enabling of debug mode.
Deeper analysis was available on the ESET blog.

_(23).jpg&h=140&w=231&c=1&s=0)








 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



