German security researchers scanning the internet have found hundreds of millions of sensitive medical images being easily accesible on unprotected servers worldwide, including around 2.6 million in Australia.
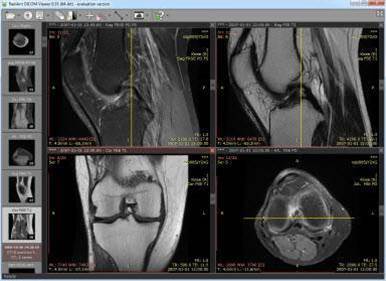
Security vendor Greenbone looked for internet-connected Picture Archiving and Communications Systems (PACS) servers that healthcare organisations use to store radiology images of patients for medical professionals to review.
With the help of scanning systems such as Shodan.io and Censys.io, the researchers found a large amount of completely unprotected PACS servers.
Greenbone discovered 590 internet-accessible PACS servers with 24 million records in 52 countries; on these, 400 million images could be downloaded with no access controls.
The Australian servers alone leaked 50,000 sets of data comprising 2.5 million accounts, with X-ray, computed tomography and magnetic resonance imaging data in them.
Beyond listing the content they found on the servers, the researchers did not identify them by location and internet protocol addresses.
Compounding the privacy breach, the systems expose patient names, dates of birth and examination, along with medical information.
The unprotected servers communicate with the Digital Imaging and Communications in Medicine (DICOM) protocol.
This uses transmission control protocol (TCP) ports 104 and 11112, often in clear text over the internet, and the researchers were able to use a DICOM viewer application to access the data.
Some of the systems provided DICOM web-based image viewers as well.
"It must be emphasised that no program development or coding was necessary to evaluate this data leak.
No exploits were written, unknown/unpublished vulnerabilities were exploited," the researchers said.
The researchers warned that the unprotected information on the servers could be exploited to obtain prescriptions, arrange for surgeries and other treatment, and to obtain bogus settlements from health insurers.
Malicious use of the exposed medical imagery on the servers to target specific individuals is another risk.
Earlier this year, Israeli researchers from the Ben-Gurion University and Soroka University Medical Centre published a study [pdf] on how attackers could tamper with 3D medical imagery with deep learning.
Attackers could "perform this act in order to stop a political candidate, sabotage research, commit insurance fraud, perform an act of terrorism, or even commit murder," the Israeli researchers wrote.
Other fraudulent uses are also possible with the personally identifiable information in the patient records, they said.
Patients could also face extortion attempts and personal attacks to disparage them and be targetted in phishing campaigns, if the confidential patient health data is exposed.
As an aside, the researchers also found more than 10,000 vulnerabilties on the PACS systems. Of these, just over 2000 are ranked as high severity, with more than 500 being classed as having a common vulnerabilties scoring system (CVSS) rating of 10.0, the worst possible.



_(37).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



