Microsoft released a temporary Fix It solution patch overnight to address a serious security issue affecting the company's Internet Explorer web browser, which is currently being actively exploited by malware writers.
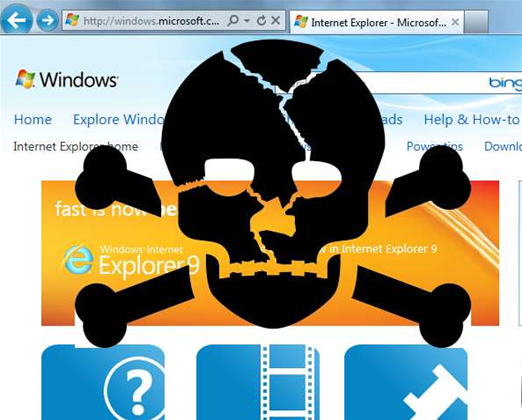
The response communications group manager of Microsoft's Trustworthy Computing department, Dustin Childs, wrote in a security advisory that the company only has reports of a limited number of targetted attacks against Internet Explorer 8 and 9.
However, the bug that allows remote code execution through users visiting a malicious website could potentially affect all supported versions of Internet Explorer, he added.
Childs did not say how many reports of the zero-day attack Microsoft has seen.
Windows Server 2003 and onwards sets Internet Explorer to run in Enhanced Security Configuration which mitigates against the vulnerability, Microsoft says. Email apps such as Outlook, Outlook Express and Windows Mail disable scripts and ActiveX controls, which also helps protect against the issue.
The security flaw is caused by Internet Explorer accessing objects in memory that have been deleted or not properly allocated. Memory can be corrupted in a way that permits attackers to run any code with the rights of the current user within Internet Explorer via visiting a specially crafted website.
Security consultant Graham Cluley said the temporary patch will not be automatically rolled out to millions of users and advised that Internet Explorer users run the Fix It solution to protect themselves.



_(28).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



