LinkedIn has fixed a flaw in its website that allowed OAuth tokens to be stolen.

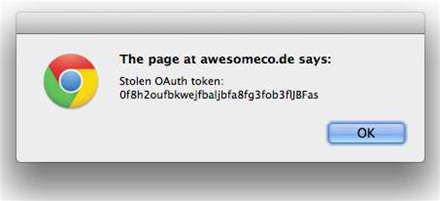
British software engineer Richard Mitchell found he could steal OAuth tokens over HTTP thanks to formerly weak authentication within an interstitial page in LinkedIn's help site.
"I quickly found a request to a JavaScript file including the API key for the help system which immediately returned an OAuth token for the user," Mitchell said.
"You shouldn’t trust JavaScript or the referer header exclusively for any kind of authorisation policy."
LinkedIn fixed the flaw on 5 July two days after it was reported and sent Mitchell a t-shirt for his effort.


.png&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



