An infosec forum was hacked and implanted with malware that hit users with drive-by attacks via a Internet Explorer zero-day.
FireEye senior malware researcher Ned Moran said evidence suggested the attackers were likely those behind the ‘Operation DeputyDog' attacks in August.
The attacks delivered the trojan.APT.9002 which could hijack machines and steal data.
“The attackers [are] able to remotely seize control of a victim's machine and exfiltrate data,” Moran said.
"We suspect that website was targeted because the attackers were interested in infecting individuals interested in US national security and international security policy.”
FireEye did not reveal the name of the hacked sites.
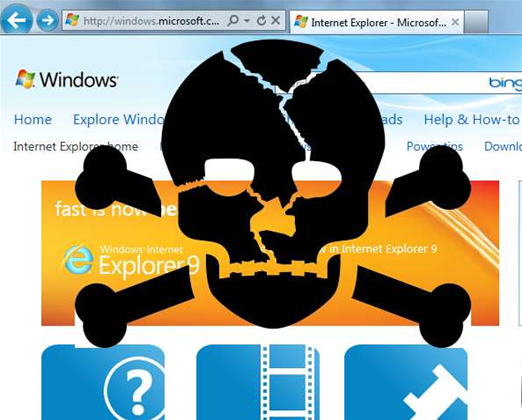
The zero-day takes advantage of a timestamp vulnerability affecting IE 7 and 8 on Windows XP and IE 9 on Windows 7, according to a post, which states that a memory access vulnerability designed to work with IE 7 and 8 on Windows XP and Windows 7 is also abused.
“The exploit targets the English version of Internet Explorer, but we believe the exploit can be easily changed to leverage other languages,” according to the post. “Based on our analysis, this vulnerability affects IE 7, 8, 9, and 10.
Until Microsoft issues an IE patch, Moran suggests that users avoid using the popular web browser.
“The fact that the attackers used a non-persistent first stage payload suggests that they are confident in both their resources and skills,” Moran said. “As the payload was not persistent, the attackers had to work quickly, in order to gain control of victims and move laterally within affected organizations.”
This zero-day vulnerability has nothing to do with a recently announced zero-day impacting versions of Microsoft Office and said by researchers to be targeting Pakistan.



.png&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



