Security researchers are reporting that servers with management interfaces exposed to the internet are being attacked by ransomware criminals who encrypt the files on the hardware in order to extort money out of victims.
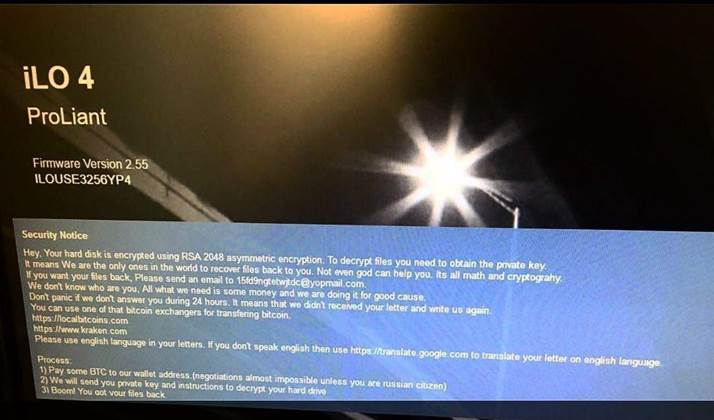
Iranian UBCERT researcher M Shahpasandi posted a screenshot of an HPE Proliant server with a ransom notice, demanding two Bitcoin (A$24,210 as of writing) for a decryption tool to unscramble files.
Other researchers said there are active internet-wide scans to identify systems running HPE's integrated lights-out (ILO 4) management interface.
Using the the Shodan.io vulnerability scanner, iTnews found 5040 systems exposing the ILO 4 interface to the internet, including 56 on Australian networks.
The attack involves brute-forcing the administrator password remotely via the Intelligent Platform Management Interface, which provides full access outside the operating system's control to server hardware.
It is relatively easy to obtain the password hash via IPMI 2.0 and to remotely crack it, previous research has shown.
Preventing password theft in this manner is currently not possible, as the mechanism to do it is part of the IPMI 2.0 specification and cannot be switched off.
Once the attacker has the password, the person can remotely mount an ISO image and execute arbitrary commands on the target server, including encrypting and wiping the files on it.
It is not known at this stage if any victims have paid the ransom and if so, if they have been successful in decrypting the files.


_(37).jpg&h=140&w=231&c=1&s=0)

_(36).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



