Google has rewarded a researcher who found his way into the inner sanctum of the online giant's vulnerability tracking system and gained access to the company's unresolved security issues.
Software developer Alex Birsan noticed that his vulnerability reports were handled by an issue tracker that Google internally called the Buganizer System, and attempted to break it out of curiosity.
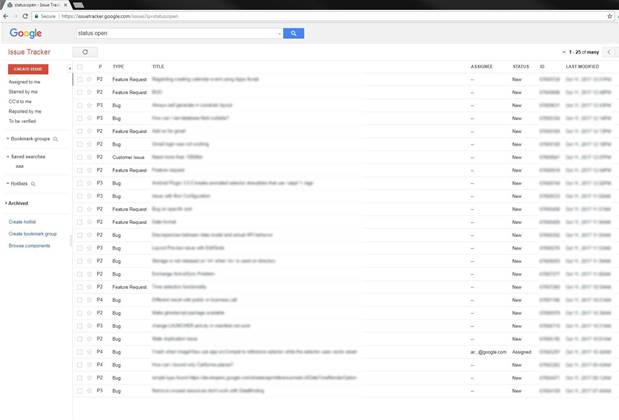
Buganizer is an in-house tool to track bugs and feature requests for product development, and is available outside Google for those that work with the company on certain projects.
Birsan observed that Buganizer handled several thousands of issues an hour, but only 0.1 percent were public.
In his attemps to gain access to the system, Birsan bypassed filters that prevented outsiders from getting a @google.com account for logins and signed up for notifications on open issues.
He noted that the issue tracker sent notifications of the vulnerablities using a particular format, with category and posting thread unique identifiers along with the @google.com domain name.
To obtain the desired @google.com login for signing into the Buganizer, Birsan used a fake email address for the issue tracker. However he didn't confirm this address and found he was able to change the email address to a new Google.com account.
Verifying the changed account, Birsan got as far as Google's corporate login page; he was still unable to fully view vulnerability reports.
The researcher then discovered another flaw where he could star issues in the Buganizer by extrapolating their identifiers, and receive notifications via email and eavesdrop on some of the issues being discussed.
Again, this turned out to be a relatively benign problem, but Birsan next found that external users could abuse oversights in the design of Buganizer's access controls to see every issue in the system's database.
Google had omitted to implement access controls in its application programming interface (API) for the Buganizer, Birsan discovered.
This meant the system did not check that the user in question was permitted to access specific issues in the Buganizer, and the system would also return full details on the flaws when querying the API.
"Yes, I could see details about vulnerability reports, along with everything else hosted on the Buganizer," Birsan wrote.
"Even worse, I could exfiltrate data about multiple tickets in a single request, so monitoring all the internal activity in real time probably wouldn’t have triggered any rate limiters."
Birsan reported the problem to Google and was rewarded with US$15,633.70 (A$20,352.38) in bug bounties for his work.


_(28).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



