Researchers have cracked encrypted user data on an Android phone by placing the device in a freezer to preserve RAM.
In doing so, they demonstrated that Android's implementation of full disk encryption, introduced in version 4 (Ice Cream Sandwich), was vulnerable to so-called cold boot attacks.
The attacks have been known for years but have not been applied to Android, the researchers said.
To demonstrate the vulnerability, a rooted - or modified - Samsung Galaxy Nexus phone was placed in a freezer and cooled to minus 15C, a temperature which extends the decay of RAM.
The battery was then ejected and reinserted in less than a second, which was fast enough to reboot the phone while keeping RAM intact.
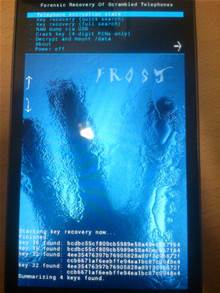
The phone was rebooted into the Android bootloader, where the FROST (forensic recovery of scrambled telephones) tool could be loaded.
"According to our results about the remanence effect, we can reboot a smartphone quickly while preserving a significant amount of RAM contents," the Erlangen University researchers wrote in a paper (pdf).
"Roughly speaking, we analyse the characteristics of the remanence effect on smartphones, prove that Android's boot sequence enable us to perform cold boot attacks, and show that valuable information can be retrieved from RAM."
The side channel attacks could be helpful to forensics professionals faced with encrypted phones.
"...Scrambled phones are a a nightmare for IT forensics and law enforcement, because once the power of a scrambled device is cut any chance other than brute force is lost to recover data."
Previous thought suggested cold-booting could preserve RAM for about 30 seconds, but the researchers found half of the available memory decayed within about six seconds at that temperature.
The encryption could be busted on only devices with open bootloaders, a feature made popular in rooted custom devices. Stock phones typically do not have open bootloaders however HTC has warmed to the process and offered assistance to users wanting to modify their devices.
But attackers could still swipe contacts, photos and emails from devices with locked bootloaders.
"After rebooting a Galaxy Nexus device, unlocking its bootloader, and booting up our recovery tool, we were still able to recover much sensitive information. Among others, we recovered emails, photos, contacts, calendar entries, WiFi credentials, and even the disk encryption key," the researchers said.
The researchers also provided tools to take forensic images of encrypted data or use brute force attacks against phone PINs.
Download the tools from the Univeristy's website.



_(28).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



