The Cyber Security Operations Centre (CSOC) arm of the Australian Signals Directorate intelligence agency responded to over a third more security incidents involving government departments last year compared to the year before, according to its 2013 report.

While the increase for 2013 wasn't as marked as the 119 percent hike recorded for the 2012 year, it was nevertheless a jump of 37 percent to 940 responses.
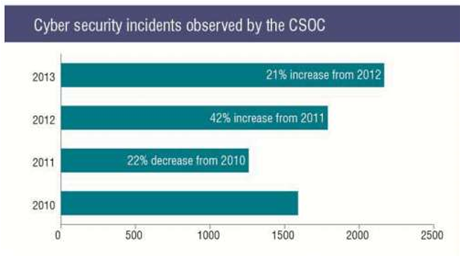
In total, the number of cyber security incidents went up by just over a fifth in 2013, hitting 2168.
Just under half of incident responses were at the federal government level, CSOC said, with local government making up 11 percent of callouts.
The vast majority of threat adversaries were what CSOC termed "foreign state sponsored." It did not reveal which states were behind the attacks on Australian government departments.
In comparison, so-called Hacktivism through groups such as Anonymous amounted to just three percent of attacks, and organised cybercrime was behind nine percent of CSOC recorded incidents.
A full two-fifths of threats were by unidentified adversaries, CSOC said.
The favoured vector of attack in 2013 was social engineering via email messages. However the proportion of email-borne attacks dropped from 63 percent in 2012 to 53 percent last year .
Attackers would try to lure victims to open attachments in messages with subjects pertaining to the G20 and ASEAN group of countries, taxation, job offers and news.
Microsoft Word files and ZIP compressed attachments containing malicious code were the two most popular types used by attackers, followed by Java .jar files, PDF documents and RAR archives.
CSOC also spotted new attacks last year, using cloud storage providers such as Dropbox to host executable code, distributing malicious Java .jar files as attachments in emails, and messages that use real, trusted email sender addresses to trick victims.
While it recognised Java as being useful due to its portability across many operating systems and computer architectures, the security centre took a swing at Australian government agencies being slack with applying updates.
"Although each new version of Java undergoes heavy scrutiny by the IT community for new security vulnerabilities, many Australian government agencies have poor patching practices, leaving them exposed to vulnerabilities that are exploited by cyber adversaries." - CSOC
Java is seen as a growing threat to Australian government networks and several strategies to stop government users from falling victim to cyber attacks are proposed by the CSOC.
These include technical measures such as hardening users applications to prevent Internet-hosted Java code from running and removing unneeded browser and PDF viewer features.
Email and web content filtering is also proposed, and CSOC also suggest that workstations and servers are based on a hardened standard operating environment that disables undesired functionality such as the next generation IPv6 Internet addressing protocol, Microsoft's LANman protocol, and autorun from optical discs and detachable storage.



_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



