Researchers have devised an analogue hardware attack that can be injected into chip components during production time, which places circuit designers relying on third-party fabrication plants at risk of shipping electronics with undetectable malware.
University of Michigan researchers Kaiyuan Yang, Matthew Hicks, Todd Austin, Dennis Sylvester and Qing Dong implemented a novel Trojan horse attack against existing hardware designs that would require a new approach to defend against, let alone detect.
Such an attack would mean companies like Apple, which designs its own processors but outsources production to chip fabrication plants, could unwittingly sell Trojanised iDevices with hardware malware that cannot be removed.
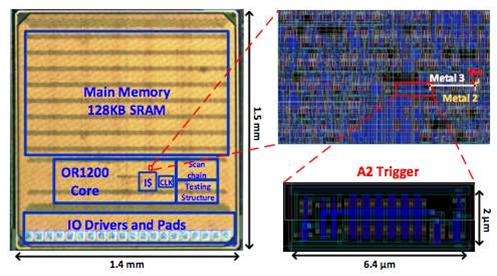
To show that such a scenario is possible, the researchers built a proof of concept using an OpenRisc OR1200 processor [pdf], and fabricated a chip that contained their A2 privilege escalation attack, which can be used to remotely take over a whole computer.
By using analogue components such as a capacitor and a few transistors wrapped up in a single logic gate to make a flip-flop with two stable states, the researchers were able to create a hardware attack that's much smaller than a digital equivalent, which requires hundreds of counter-based triggers.
To trigger the attack, the capacitor in the researchers' A2 gate siphons off charge from a target wire on the chip. When attached to a signal that toggles between high and low states infrequently through interaction with normal software, the capacitor doesn't charge sufficiently, and the attack doesn't trigger.
However, if the signal is toggled at high rates using a specially crafted operating system user mode program, the capacitor charges fully and the flip-flop changes state.
This flips the bit that switches between user and supervisor mode, escalating the access rights to the systems for the attack.
The reseachers said that while fabrication-time attacks have been studied over the past ten years, their A2 exploit is small and changes just a single chip gate. This makes it stealthy, and extremely hard to detect.
While the researchers used the open source OR1200 processor for their proof of concept, they said it was possible to build A2-like attacks into Intel and AMD x86 architecture chips.
"We expect a A2-like attack in x86 processors to be much harder to detect and easier to implement than its OR1200 counterpart," the researchers wrote.
"While there are more viable victim registers in x86, A2 still only needs to target a single register to be effective."
Chip design companies try to spot errors in integrated circuits with post-fabrication testing, but the A2 attack is unlikely to be spotted as it requires a sequence of trigger events that even the most meticulous tester won't ever encounter, the researchers said.
In fact, the only way to effectively detect the subverted chips would be to de-layer them, and image each with a scanning electron microscope. This, however, is prohibitively expensive.
Detecting hardware Trojans at the digital level isn't possible either, as operating systems fully trust the processors they run on.
Defending against chip-level attacks is very difficult. The researchers worked out ways to defeat existing defence methods such as on-chip sensors, side-channels and chip characterisation or fingerprinting with A2.
They proposed a new type of defence, where trusted circuits monitor the execution of untrusted circuits, and look for digital behaviours that are out of specification for the chip.
Low-level attacks that subvert hardware have been devised before. Bell Labs UNIX developer Ken Thompson, inventor of the B (a precursor to C) and Go languages, devised an attack that could be implemented in hardware microcode, to inject a backdoor.




.png&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



