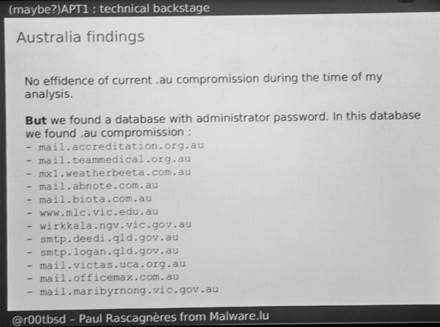
A researcher who hacked a Chinese cracking group found website credentials for a dozen Australian government and private domains on a server owned by the group.
Paul Rascagneres (@r00tbsd) of research outfit malware.lu told the Breakpoint security conference in Melbourne today that he did not know why the cracking group known as APT1 had targeted the websites or if the organisations were compromised.
The affected government sites included Queensland's Department of Employment, Economic Development and Innovation and low key targets including mail servers for local councils Maribyrnong and Logan.
The credentials were uncovered on an APT1 server following Rascagneres' offensive research into the group. In that work he compromised the group's Remote Access Trojan (RAT) and server infrastructure.
He said the APT1 group was seeking information on company tenders.
"When I scan [APT1's infrastructure] the attackers shut down -- it was a game between this guy and me," Rascagneres said.
His research followed a detailed Mandiant report on the APT1 group but went went further because he hijacked the cracker's command and control servers and their RATs.
In its work, Malware.lu wrote a custom extension of the password cracker tool John the Ripper to specifically target the Poison Ivy trojan, then exploited a known buffer overflow vulnerability in Ivy's command and control infrastructure. The group also wrote a tweaked Metasploit module to make the latter exploit more effective.
The bold research paper earned Rascagneres a much-lauded Pwnie Award at this year's BlackHat conference in Las Vegas. [pdf]





_(33).jpg&h=140&w=231&c=1&s=0)

_(37).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



