The days of ordinary users installing any software they like on Windows could be numbered as Microsoft tightens up the security for its desktop and laptop operating system.

An early version of what Microsoft calls application installation control (AIC) appeared in its preview insider build 15046 for users who have selected to receive new features early.
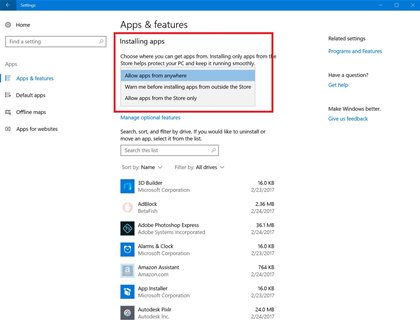
As the name implies, AIC provides systems administrators control over the types of apps that can be installed on a personal computer running Windows.
Similar to Apple's Gatekeeper feature, AIC can be set to allow apps from any source, or only from the Windows Store. Alternatively, AIC can warn if users attempt to install an app from other sources than the app store, Microsoft said.
The warning message will direct users to the store where they can download equivalent apps vetted for security by Microsoft, if available.
AIC is set by default to allow apps from anywhere, and Microsoft did not say if it intends to change that setting to a more restrictive one.
Apple has had the similar Gatekeeper feature in OS X since 2012. It enforces code signing and application verification before the code is allowed to execute.
Gatekeeper is credited with reducing Mac malware infestations, and Apple recently strengthened the security feature with path randomisation for application bundles and signed disk images.





_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit












_(1).jpg&h=140&w=231&c=1&s=0)



