Adobe was preparing to fix a chief source of portable document format security vulnerabilities with the implementation of a "sandbox" in the next major revision of its popular Reader software.

A sandbox in industry parlance isolated software from the rest of the PC and its programs including the operating system that could be compromised by malicious code.
This "protected mode" in the PDF Reader software was based on Microsoft's practical windows sandbox and engineering smarts from search-advertising giant Google, said Adobe senior director of product security and privacy Brad Arkin.
Adobe Reader 10, due by the end of the year, will protect users from hackers' unauthorised attempts to write or modify the contents of their PCs using corrupted or malformed PDF files, Arkin said.
For instance, an attacker will be denied the ability to install through a PDF malicious software on a PC such as a virus or Trojan or to delete files or meddle with the operating system without the user's consent.
And malware writers were similarly prevented from modifying system information.
Later, a "dot" or minor release, will block illicit attempts to read data.
"A sandbox is something that allows us to run an application with lower rights," Arkin said. "Even if an attacker is able to identify a potential vulnerability the impact of an exploit is mitigated because the attacker can't get out of the sandbox.
"Even if [hackers] find a vulnerability they will end up stuck in sandbox and it would require a second stage of attack to get access to the resources in the machine".
Adobe used the same techniques in Microsoft's Office 2010 productivity software and Google's Chrome web browser.
Sandboxes were seen as a superior solution to the problem of securing software against attack while allowing users freedom to interact with their PCs and software without the annoyance of interruptions through pop-up windows requesting access to device resources, Arkin said.
The approach had currency with internet browser makers such as Google and the Mozilla Firefox project, which collaborated on Project Pepper to secure the next generation of software. A similar approach to Pepper's sandbox was behind the security that protected Dell's Kace subsidiary browser software from hackers.
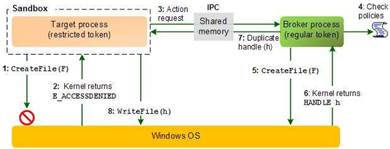 |
| Plugging the write hole in Adobe Reader. source: Adobe |
Contemporary versions of Adobe Reader allowed attackers to piggyback on legitimate workings of the software as it accessed files, the Registry, memory and core operations of the operating system ("kernel").
Following the upgrade, holes such as these opened when the PDF tried to write to a temporary folder such as when filling forms or launching an attachment will be blocked by default.
To carry out these operations, requests for other actions were funnelled through a "broker", a process with full rights to the inner workings of the PC and that determined the access allowed (see graphic).
In the example Arkin gave, the PDF may access its version number or digital signature but not the contents of the Windows root directory as was now the case.
Although he said the update was no "silver bullet" to the problem of Reader vulnerabilities, fixing the write hole on Windows machines "mitigates" the threat for "as many users as possible, as fast as possible from as many real-world threats as possible" without degrading performance.
For instance, it wouldn't protect against other popular attacks such as:
- "Clickjacking" - Taking a user to a website they didn't intend to visit;
- Phishing - Where an attacker masquerades as a trusted source in an attempt to wheedle an innocent user's out of their private information;
- Weak cryptography, or;
- Unauthorised network access
"Our intelligence from what is happening in terms of real-world attacks, the attacks people are experiencing, is the type of thing like a drive-by attack" used to recruit an innocent PC into a botnet or swarm of infiltrated PCs that are turned loose to attack networks, Arkin said.
"Those are of most value to attackers when they are installing malicious software to gain control of a machine."
But he cautioned users to be careful when upgrading their software because hackers were likely to use the publicity around the new, more secure Reader to compromise their systems by directing them to unauthorised websites hosting malicious code.
Users should either use the automated update function in earlier versions of Adobe Reader to upgrade or carefully check the digital signature to ensure the software was from Adobe, he said.
What about Mac and Linux?
But because sandboxes were dependent on their host platform, the Windows experience won't translate to Reader software on other systems, he said. Although that was unlikely overly to bother users of other operating systems.
"From a percentage breakdown, the vast majority of users are on the Windows platform and when we look at attacks in the real world they almost always occur against Windows users.
"For any individual bug there's a good chance it's present on Mac and Linux because [Reader] is a shared codebase but, in reality, almost none of those bugs are exploited in the wild."
The relationships Adobe and Google built through their products stood the software maker in good stead when it came to hardening Reader.
"At the engineering level where most conversations happen they were eager to share their experience and learn from us because we were doing a lot of things that went beyond the boundaries of what had happened before," Arkin said.
"Google and Adobe are close partners particularly when you look at Flash player and integration with Chrome and Android and the Reader team in Adobe also has a good relationship with Chrome and Android teams."
A result of the new architecture was that there was the possibility that older PDFs could break in the new security environment. Although he acknowledged this possibility, Arkin said Adobe's "No 1 mandate is not to break or disrupt user workflows".
Government and business are big users of PDFs to streamline their workflows. For instance, the overburdened Australian Electoral Commission uses interactive Adobe PDF forms for change of enrolment prior to tomorrow's deadline for the August 21 poll.
"It's certainly possible given the billions of PDF files out there that one of them is not compatible with sandboxing but we haven't found it yet."



.png&h=140&w=231&c=1&s=0)

_(28).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



