The process for IT admins to assign users to corporate SaaS applications varies according to the complexity of the app and the depth of integration Microsoft has negotiated.
Azure AD also recognises role-based access for some of these deeper integrations (as per Salesforce example above). It would be prudent to first check with Microsoft just how deep each integration is with the SaaS apps you're already using to ensure Azure AD offers the necessary granularity.
At this stage, Azure AD doesn't offer a lot of features for managing group policy. It does offer a global approach to user password resets, which is well thought-out. Stay tuned for more in this space - a few more group policies would be a welcome addition.
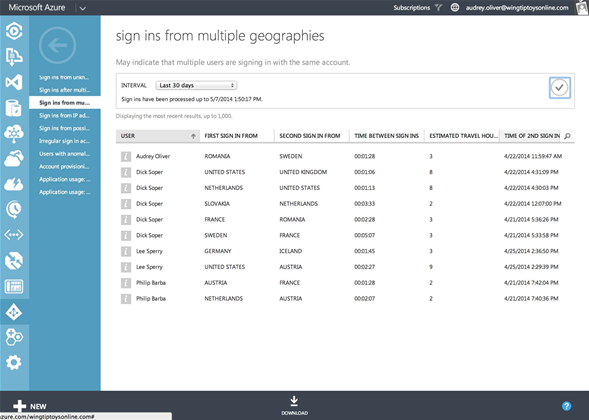
Engineers we spoke to about the feature conceded that they aren't confident enough in it yet to start automating responses to these anomolies - preferring instead to raise flags with admins who, from the same screen, can choose to revoke access or prompt a multi-factor log-in.
It's ideas like these that demonstrate the latent potential for Azure AD to be a great service, but it would be premature to say it is production-ready just yet.
Product managers told iTnews to expect the Azure cloud to gain a richer feature set over time as "there are things you can do in the cloud at scale that you simply can't do on-prem."
If Microsoft does get this service right, Azure AD has the potential to maintain Redmond's status as the identity manager of choice at a time when Citrix, Google, IBM, VMware and others are knocking on the door.








_(33).jpg&h=140&w=231&c=1&s=0)

_(23).jpg&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



