Features

Cyberspace, the wild frontier

Is risk an overused buzzword?

Make mobility a part of your strategy

USB flash in the Lan

Try to turn SOX into an opportunity
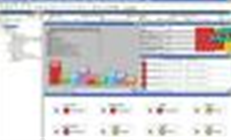
Review: ArcSight ESM
ArcSight's flagship product, the ArcSight Enterprise Security Manager, is a security event management (SEM) tool capable of analyzing large mounts of network data in real time. The IDS model fell down because the flood of unfiltered alerts overwhelmed the resources of security teams, but SEM provides correlation, filtering and analysis to, in theory, allow the few real threats to be picked out of the blizzard of less important alerts and false positives.

Don't buy your way out of trouble

Review: FortiGate 5020
Fortinet's FortiGate 5020 is built using a powerful chassis containing dual, hot-swappable power supplies as standard, building in redundancy. The chassis can also house two 5001 blades, each of which comes with four copper Gigabit Ethernet ports and four small, form-factor pluggable (SFP) ports.

Review: Internet Security & Acceleration Server 2004 Enterprise Edition
Microsoft's Internet Security & Acceleration (ISA) Server 2004, is the company's application for turning a Windows 2000 or 2003 server into an enterprise firewall. Installation was painless on our test Windows 2003 server.











