It is more important to bring users into an encryption ecosystem than it is to come up with the next release
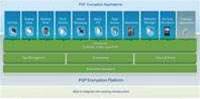
Why then have encryption at all? One school of thought is that encryption is everything. It is the security on the enterprise. The other is that encryption is something you add if information on the enterprise happens to be extraordinarily sensitive.
PGP's position differs a bit from either of these. Encryption, according to a PGP visionary, works in ways that other security measures do not. Encryption is a core piece of any security architecture and needs to work with other security measures. That approach has characterised PGP's vision for the future.
The PGP platform is generic to the point that it will run on just about anything — from a mainframe to a PDA. This makes it extremely extensible and scalable. The most important part of the vision, however, is the notion of competition.
According to PGP, encrypting techniques need to be abstracted as far away from the user as possible.
Other objectives for the future include expanding encrypting of mass storage, bringing more people into an encryption ecosystem with as little inconvenience as possible, and extending key management to much larger and more complicated environments.
We felt that the view of the overall secure environment over the narrower view of encryption as “the answer” was innovative. Encryption, then, becomes an integral part of the architecture, and managing it, making it work for the average user, is as important as — arguably more so than — the encryption itself.
See original article on SC Magazine US


_(33).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



