There are no limits on the amount collected per day and the L7400x is restricted to a rate of 100,000 events per second (EPS). The L7400x looks quite capable of handling this amount of traffic. We couldn't generate that much data in the lab, but, with our sources throwing around 400 syslog EPS at the appliance, this didn't even tickle its CPU, with utilisation rarely creeping above two per cent.
Logger is designed to collect and store events, provide long-term secure storage for regulatory compliance and deliver high-speed data analysis and reporting functions. The appliance can also be configured to send out real-time alerts when specific event patterns have been detected.
The list of supported log sources is enormous and includes all syslog sources over UDP and TCP and raw file based logs via protocols such as FTP, SCP and SFTP. Most of the rest are covered by ArcSight's SmartConnectors, which collect and normalise native logs from around 300 device types. ArcSight's FlexConnectors are used to build receivers for unlisted legacy devices, systems and applications.
Deployment is swift and, although nowhere near as slick as McAfee's NitroSecurity products, Logger's management interface is simple to use making further configuration easy. To collect log data your first task is to create receivers and both TCP and UDP syslog servers are defined by default. We had a variety of syslog sources in the lab including firewalls, UTM devices, network switches and storage appliances, and all we had to do was point their syslog servers at the IP address of the appliance.
The moment the appliance started to see incoming log data, it created new receivers for each device. To make things clearer you can manually edit each entry with more information about each device. To send Windows Event Log data to the appliance we installed the Windows Unified Connector version on a Windows Server 2008 R2 system. Once loaded, you can use a wizard to set up domain authentication, enter the systems you want to retrieve logs from and select application, security and system logs.
The only other task is to create a corresponding receiver on the appliance for the SmartConnector. The process is simple enough although the SmartConnector interface for entering each Windows system, their credentials and log selection is too small and the columns have to be adjusted so you can see what you're doing.
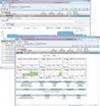
The interface's home page opens with a basic summary of log activity for all receivers along with CPU and storage utilisation. Unlike LogLogic's SIEM products, you don't get a real-time viewer showing messages; to view events you have to go to the Analyze section. This provides a search facility where queries are created using keywords, time ranges and Boolean expressions. This is the most complex part of Logger as there are a lot of operators to get used to, although the manual makes a good job of explaining their use.
Simple queries can be created using keywords and we found the results were speedily returned. A graph shows all occurrences of the search parameters for the time period and you can drill down by selecting one of its bars.
More complex queries can be built up easily with a few mouse clicks to filter the results. Details of each log entry matching the initial search criteria are shown in the lower window, and selecting any of these fields adds them as extra operators. Reporting features are excellent and can be customised. Regulatory compliancy reporting is also available, although these packages are all optional. However, once your licences are applied you can access an extensive list of predefined reports for regulations such as PCI DSS, SoX and HIPPA. Real-time alerts use queries or filters linked with thresholds and notification destinations such as email, SNMP trap receivers or ArcSight's own ESM products. If you opt for one of the regulatory reporting options these also include predefined alerts for suspect activities.
Storage is managed by combining storage groups with rules. These determine where data from specific device groups is stored and what data retention policies are applied. Events, alerts and search data can also be archived to remote CIFS and NFS shares.
Dave Mitchell
An enterprise-class log management solution with a very high collection rate and quality analysis and reporting tools


_(33).jpg&h=140&w=231&c=1&s=0)

_(20).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



