In the first quarter of 2020, within a matter of weeks, our way of life shifted. We’ve become reliant on online services more than ever. Employees that can are working from home, students of all ages and grades are taking classes online, and we’ve redefined what it means to stay connected.

The more the public is dependent on staying connected, the larger the potential reward for attackers to cause chaos and disrupt our way of life.
It is therefore no surprise that in Q1 2020 (January 1, 2020 to March 31, 2020) we reported an increase in the number of attacks—especially after various government authority mandates to stay indoors went into effect in the second half of March.
In Q2 2020 (April 1, 2020 to June 30, 2020), this trend of increasing DDoS attacks accelerated:
- The number of L3/4 DDoS attacks observed over our network doubled compared to that in the first three months of the year.
- The scale of the largest L3/4 DDoS attacks increased significantly. In fact, we observed some of the largest attacks ever recorded over our network.
- We observed more attack vectors being deployed and attacks were more geographically distributed.
The number of global L3/4 DDoS attacks in Q2 doubled
Gatebot is Cloudflare’s primary DDoS protection system. It automatically detects and mitigates globally distributed DDoS attacks. A global DDoS attack is an attack that we observe in more than one of our edge data centres. These attacks are usually generated by sophisticated attackers employing botnets in the range of tens of thousand to millions of bots.
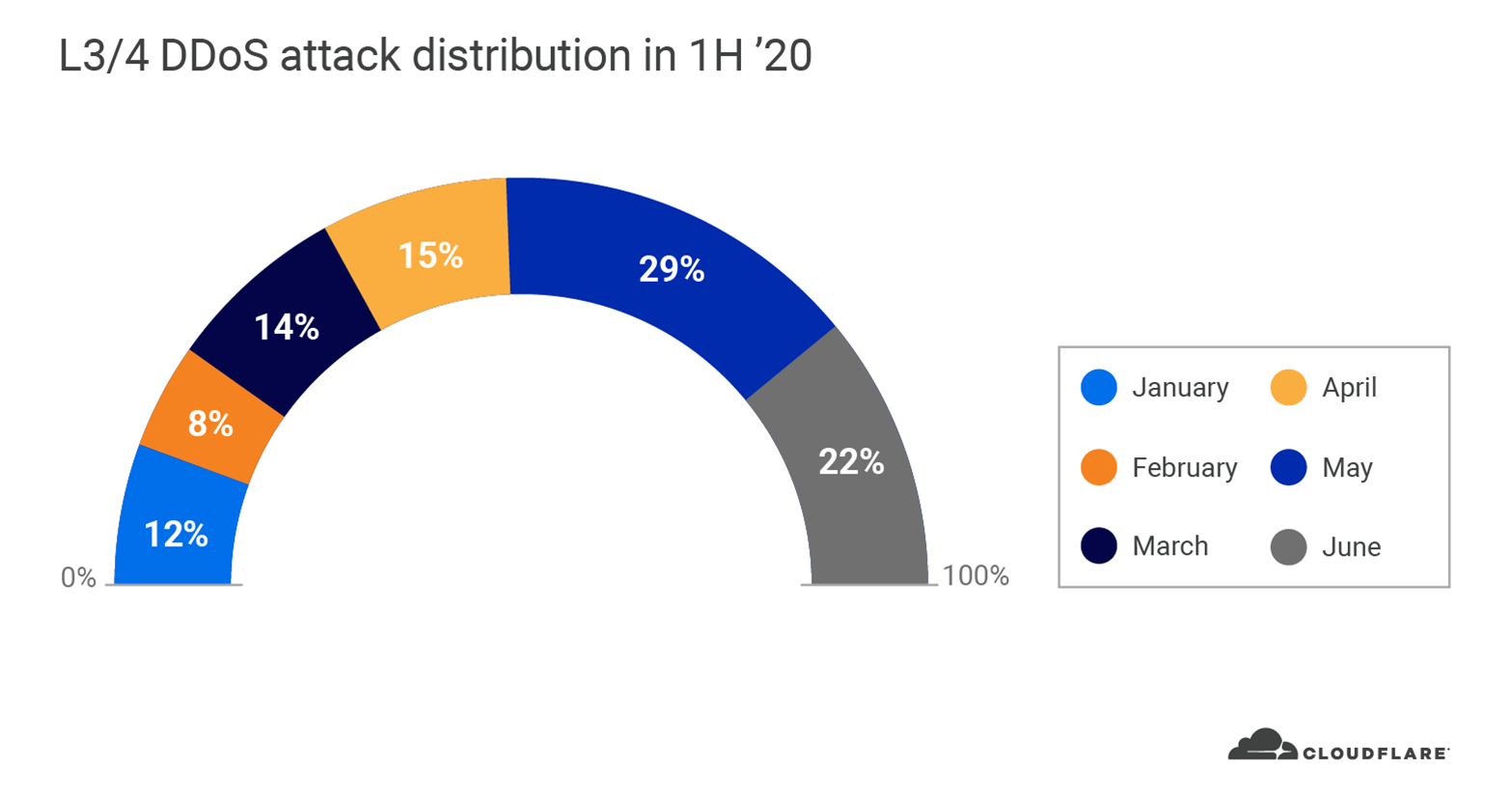
Sophisticated attackers kept Gatebot busy in Q2. The total number of global L3/4 DDoS attacks that Gatebot detected and mitigated in Q2 doubled quarter over quarter. In our Q1 DDoS report, we reported a spike in the number and size of attacks. We continue to see this trend accelerate through Q2; over 66 per cent of all global DDoS attacks in 2020 occurred in the second quarter (nearly 100 per cent increase). May was the busiest month in the first half of 2020, followed by June and April. Almost a third of all L3/4 DDoS attacks occurred in May.
In fact, 63 percent of all L3/4 DDoS attacks that peaked over 100 Gbps occurred in May. As the global pandemic continued to heighten around the world in May, attackers were especially eager to take down websites and other Internet properties.
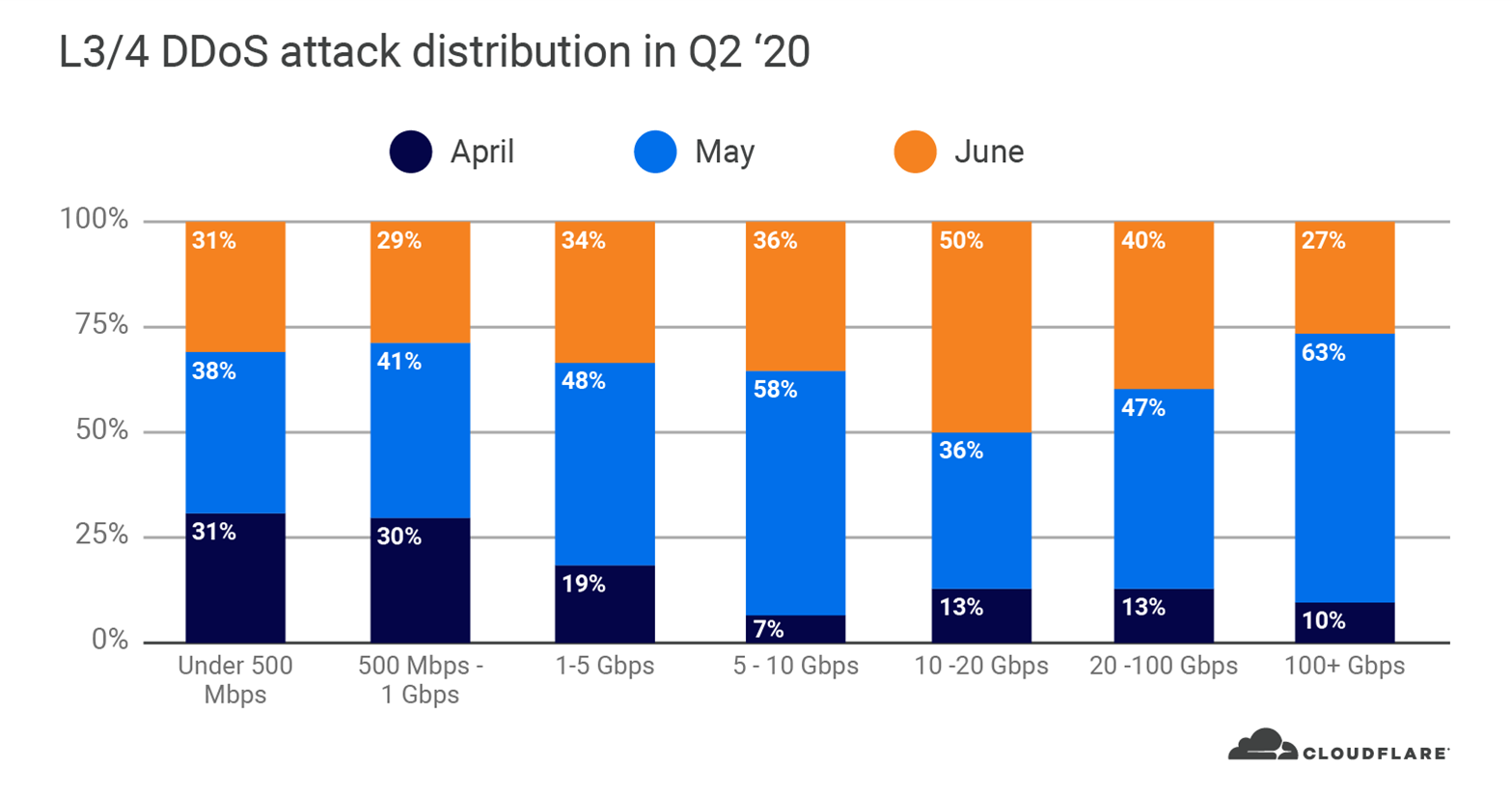
Small attacks continue to dominate in numbers as big attacks get bigger in size
A DDoS attack’s strength is equivalent to its size—the actual number of packets or bits flooding the link to overwhelm the target. A ‘large’ DDoS attack refers to an attack that peaks at a high rate of Internet traffic. The rate can be measured in terms of packets or bits. Attacks with high bit rates attempt to saturate the Internet link, and attacks with high packet rates attempt to overwhelm the routers or other in-line hardware devices.
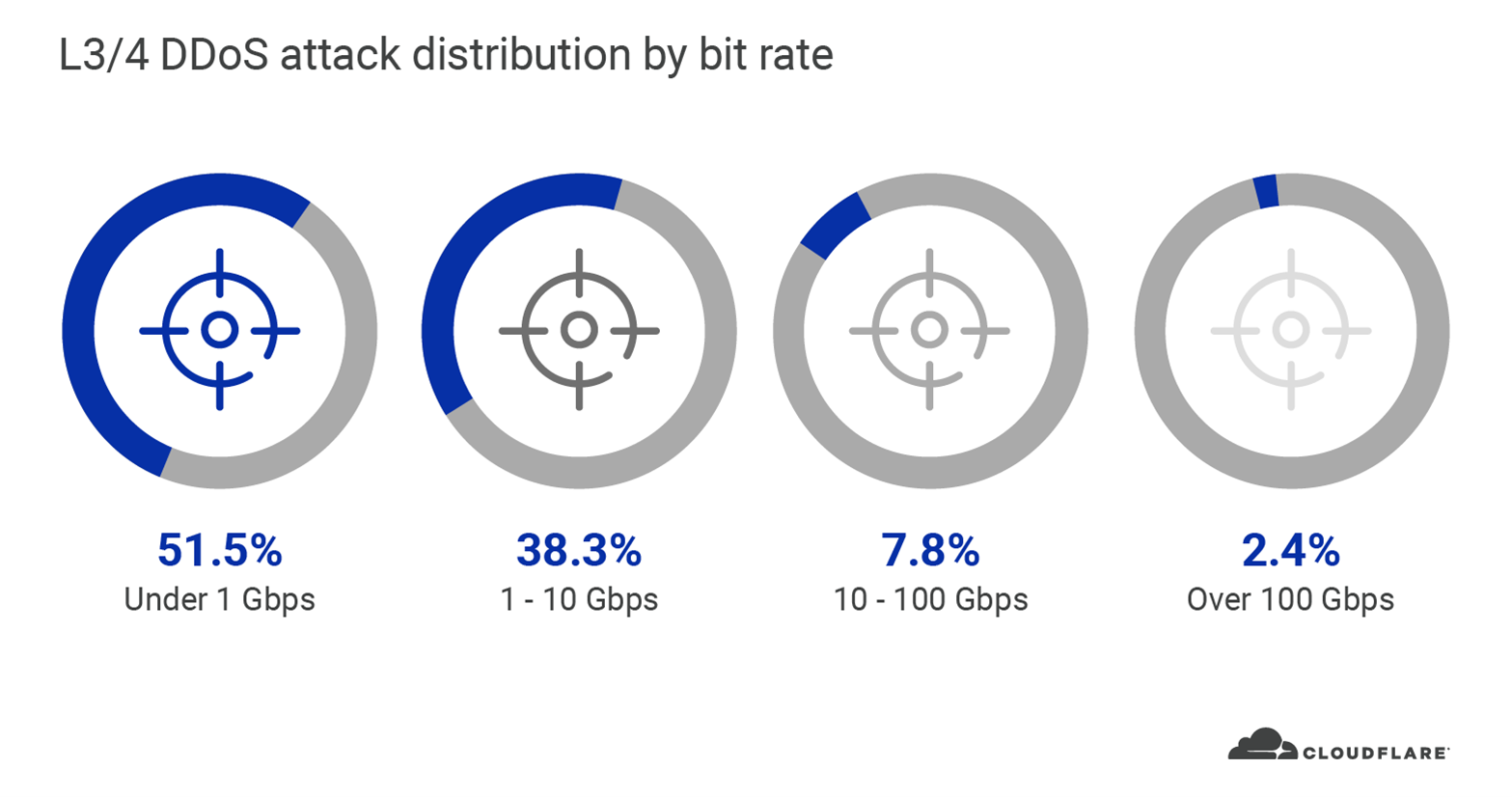
Similar to Q1, the majority of L3/4 DDoS attacks that we observed in Q2 were also relatively ‘small’ with regards to the scale of Cloudflare’s network. In Q2, nearly 90 per cent of all L3/4 DDoS attacks that we saw peaked below 10 Gbps. Small attacks that peak below 10 Gbps can still easily cause an outage to most of the websites and Internet properties around the world if they are not protected by a cloud-based DDoS mitigation service.
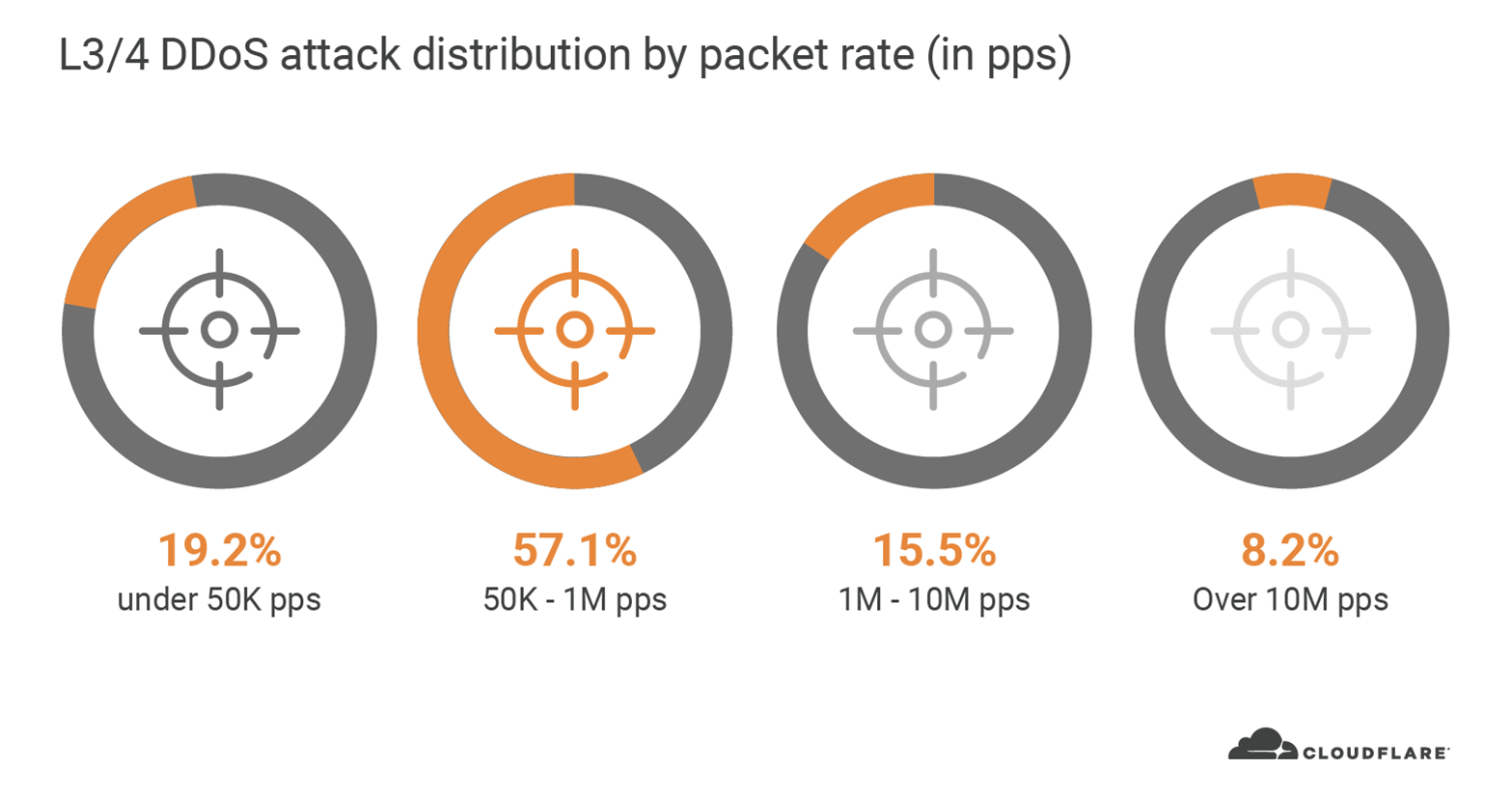
Similarly, from a packet rate perspective, 76 per cent of all L3/4 DDoS attacks in Q2 peaked up to 1 million packets per second (pps). Typically, a 1 Gbps Ethernet interface can deliver anywhere between 80k to 1.5M pps. Assuming the interface also serves legitimate traffic, and that most organisations have much less than a 1 Gbps interface, you can see how even these ‘small’ packet rate DDoS attacks can easily take down Internet properties.
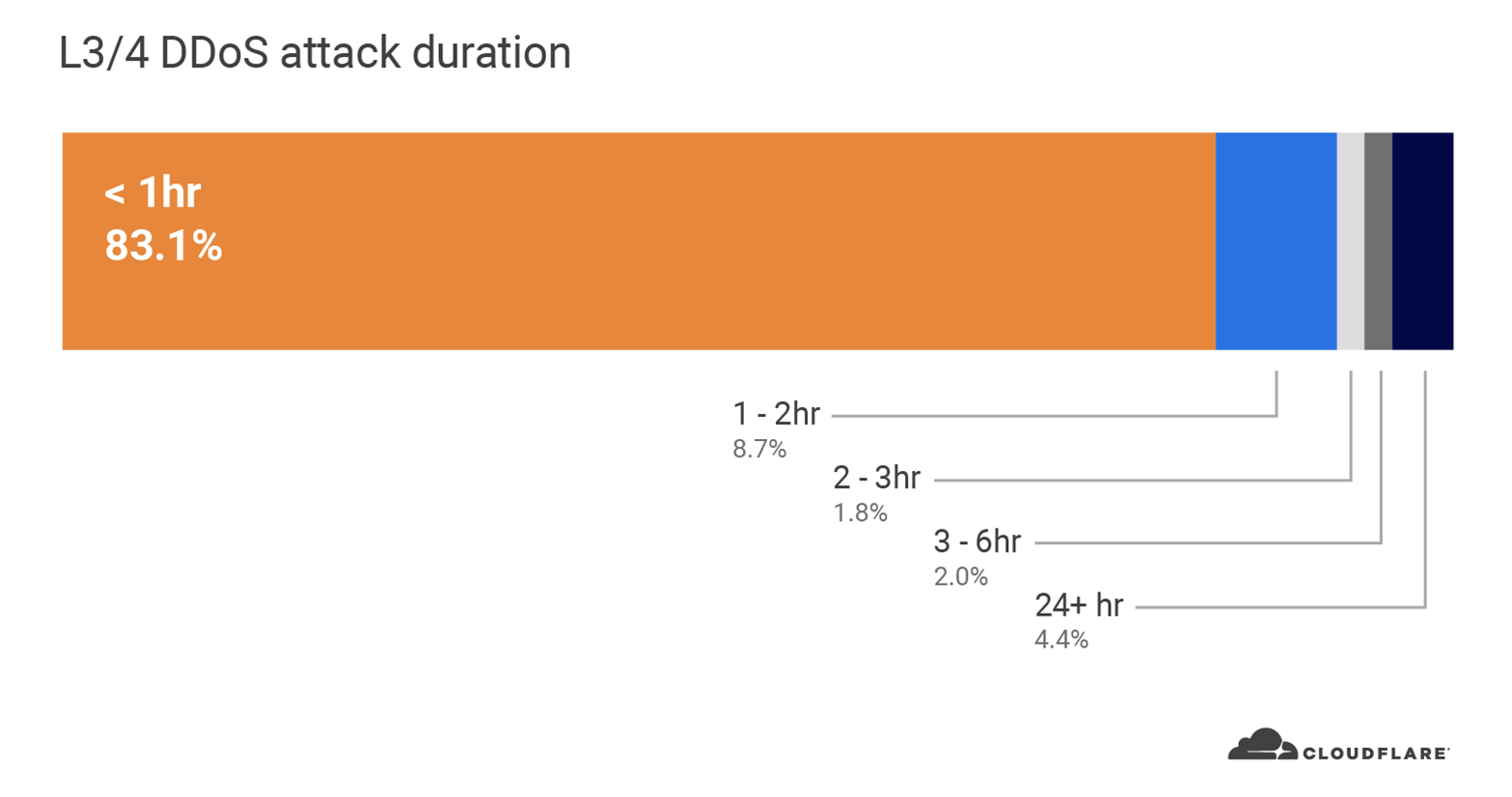
In terms of duration, 83 per cent of all attacks lasted between 30 to 60 minutes. We saw a similar trend in Q1 with 79 per cent of attacks falling in the same duration range. This may seem like a short duration, but imagine this as a 30 to 60 minute cyber battle between your security team and the attackers. Now it doesn’t seem so short. Additionally, if a DDoS attack creates an outage or service degradation, the recovery time to reboot your appliances and relaunch your services can be much longer; costing you lost revenue and reputation for every minute.
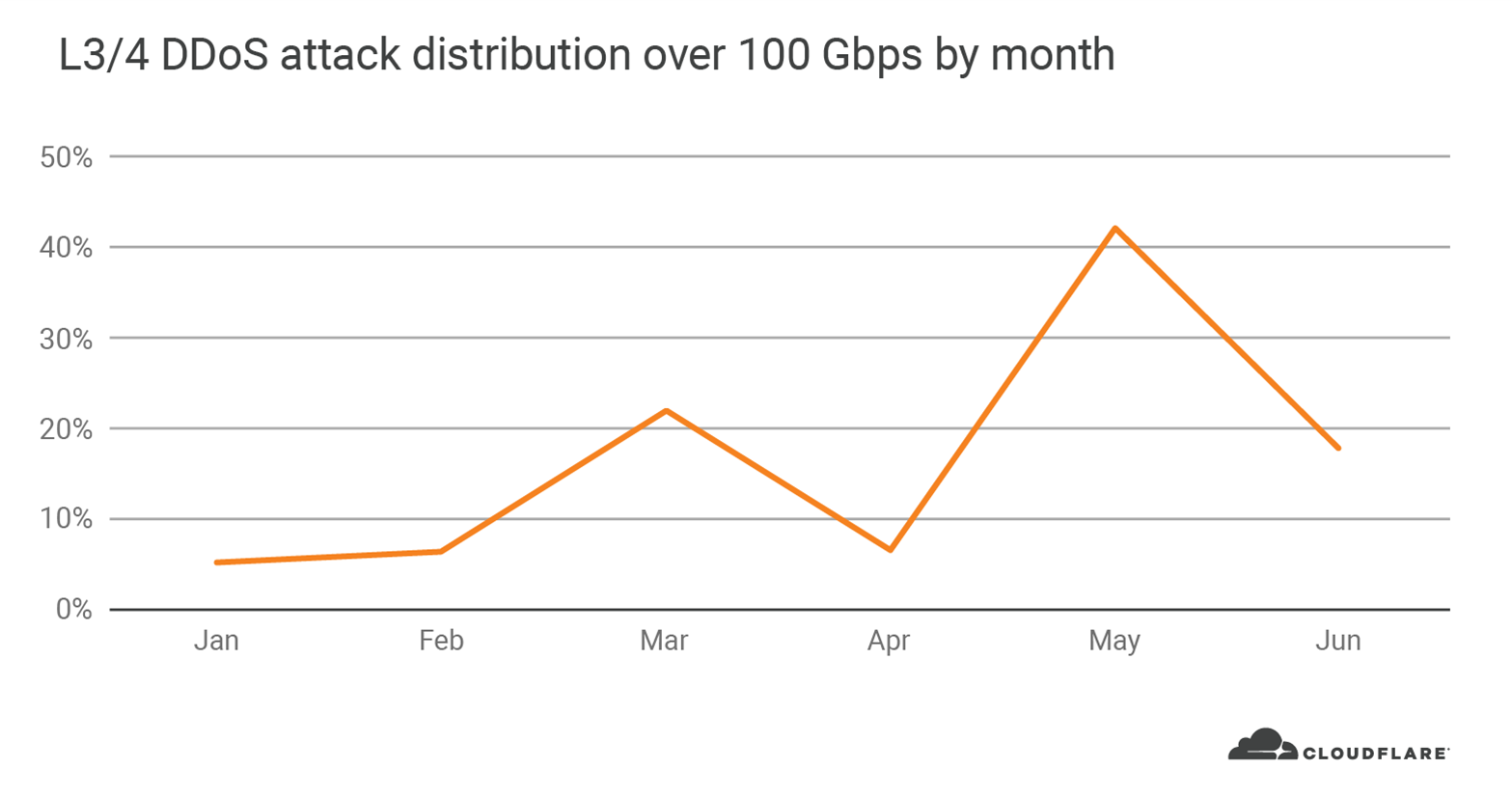
In Q2, we saw the largest DDoS attacks on our network, ever
In Q2, we saw an increasing number of large scale attacks; both in terms of packet rate and bit rate. In fact, 88 per cent of all DDoS attacks in 2020 that peaked above 100 Gbps were launched after shelter-in-place went into effect in March. Once again, May was not just the busiest month with the most number of attacks, but also the greatest number of large attacks above 100 Gbps.
The risk to local organisations was illustrated in late August, when New Zealand’s stock exchange fell victim to DDoS attacks. The exchange experienced multiple days of interruption due to the incident.
To learn more about DDoS attacks, watch Cloudflare’s webinar to learn about the various approaches DDoS attackers are using right now, and what forward-thinking organisations are doing in response to these trends and tactics. Watch the on-demand webinar here.








