DDoS attacks are surging in frequency and sophistication – in this article, we cover some of the key issues for IT security teams.

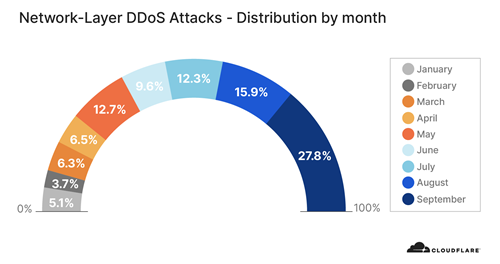
After doubling from Q1 to Q2, the total number of network layer attacks observed in Q3 doubled again — resulting in a 4x increase in number compared to the pre-COVID levels in the first quarter.
Here are some other key network layer DDoS trends we observed in Q3:
- Majority of the attacks are under 500 Mbps and 1 Mpps — both still suffice to cause service disruptions
- We continue to see a majority of attacks be under 1 hr in duration
- Ransom-driven DDoS attacks (RDDoS) are on the rise as groups claiming to be Fancy Bear, Cozy Bear and the Lazarus Group extort organisations around the world. See a special note on this below.
Number of attacks
The total number of L3/4 DDoS attacks we observe on our network continues to increase substantially, as indicated in the graph below. All in all, Q3 saw over 56 per cent of all attacks in 2020 — double that of Q2, and four times that of Q1. In addition, the number of attacks per month increased throughout the quarter.
Attack size (bit rate and packet rate)
There are different ways of measuring a L3/4 DDoS attack’s size. One is the volume of traffic it delivers, measured as the bit rate (specifically, Gigabits-per-second). Another is the number of packets it delivers, measured as the packet rate (specifically, packets-per-second). Attacks with high bit rates attempt to saturate the Internet link, and attacks with high packet rates attempt to overwhelm the routers or other in-line hardware devices.
In Q3, most of the attacks we observed were smaller in size. In fact, over 87 per cent of all attacks were under 1 Gbps.
Note that, even ‘small’ attacks of under 500 Mbps are many times sufficient to create major disruptions for Internet properties that are not protected by a Cloud based DDoS protection service.
This trend holds true for attack packet rates. In Q3, 47 per cent of attacks were under 50k pps — compared to just 19 per cent in Q2.
Smaller attacks can indicate that amateur attackers may be behind the attacks — using tools easily available to generate attacks on exposed IPs/ networks. Alternatively, small attacks may serve as a smokescreen to distract security teams from other kinds of cyberattacks that might be taking place simultaneously.
Attack duration
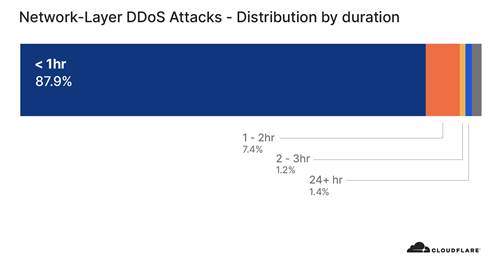
In terms of length, very short attacks were the most common attack type observed in Q3, accounting for nearly 88 per cent of all attacks. This observation is in line with our prior reports — in general, Layer 3/4 DDoS attacks are getting shorter in duration.
Short burst attacks may attempt to cause damage without being detected by DDoS detection systems. DDoS services that rely on manual analysis and mitigation may prove to be useless against these types of attacks because they are over before the analyst even identifies the attack traffic.
Alternatively, the use of short attacks may be used to probe the cyber defences of the target.
Whatever their motivation, DDoS attacks of any size or duration are not going away anytime soon. Even short DDoS attacks cause harm, and having an automated real-time defense mechanism in place is critical for any online business.
Attack by country
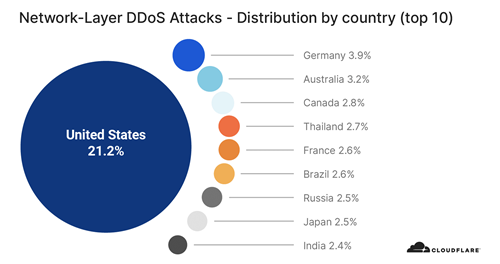
Looking at country-based distribution, the United States observed the most number of L3/4 DDoS attacks, followed by Germany and Australia.
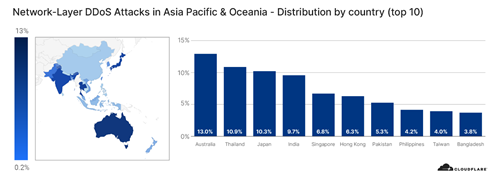
Asia Pacific & Oceania
A note on recent ransom-driven DDoS attacks
In 2020, Cloudflare observed another disturbing trend — a rise in extortion and ransom-based DDoS (RDDoS) attacks targeting organisations around the world. While RDDoS threats do not always result in an actual attack, the cases seen in 2020 showed that attacker groups are willing to carry out the threat, launching large scale DDoS attacks that can overwhelm organisations that lack adequate protection. In some cases, the initial teaser attack may be sufficient to cause impact if not protected by a Cloud based DDoS protection service.
In a RDDoS attack, a malicious party threatens a person or organisation with a cyberattack that could knock their networks, websites, or applications offline for a period of time, unless the person or organisation pays a ransom.
To receive the latest news on DDoS trends, subscribe to Cloudflare's blog. You can also register for the upcoming Cloudflare and iTnews webinar on February 18, 2021, to learn how you can protect yourself from DDoS attacks in 2021.








