Recent articles by Jon Tullett

Review: Cyber Alert
Author Peter Warren and Michael Streeter

Review: Windows Server 2003 Security, Volume 2
Author Roberta Bragg

Review: The Art of Intrusion
Author Kevin Mitnick & William Simon

Review: The Black Book on Corporate Security
Publisher Larstan
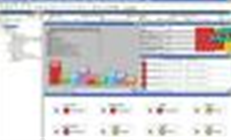
Review: ArcSight ESM
ArcSight's flagship product, the ArcSight Enterprise Security Manager, is a security event management (SEM) tool capable of analyzing large mounts of network data in real time. The IDS model fell down because the flood of unfiltered alerts overwhelmed the resources of security teams, but SEM provides correlation, filtering and analysis to, in theory, allow the few real threats to be picked out of the blizzard of less important alerts and false positives.

Review: LogMeIn
When 3am Labs asked us to review LogMeIn, we were not sure whether it was really appropriate for SC Magazine. The software is primarily a tool for web-based remote access and administration (there is a "network console" version for enterprise administrators, too). But it has a surprisingly broad set of security features, as well as some clever ways to tie down possible vulnerabilities in remote administration.

Review: DESlock+
We have looked at DESlock+ before, with its DESkey USB tokens and file encryption software. And while the previous version impressed us enough to win Best Buy in our Data Encryption test last year, it is safe to say that the product has been improved by leaps and bounds since then.













