When Australia Post employees stopped responding to internal phishing campaigns designed to test staff security awareness, the organisation's infosec team knew they had to shake things up.
Eight months ago, when the team sent out one of their bi-monthly phishing drives, more than half of those who fell for the fake email said they weren’t at all stressed about the fallout.
A further 43 percent of that same group said they were confident they’d never fall for a phish - but still did - while a growing number of others said they knew they were being phished, but decided to click on the dodgy link anyway “for the lulz”.
And all of those who clicked on the link, which took staff to training materials on how to spot phishing, abandoned the training in under 30 seconds.
“No matter what we gave them to click on, they knew they’d mucked up and went ‘I’m out’,” AusPost infosec awareness specialist Adam Janik told the ACSC 2017 conference this week.
“We just weren’t getting the right effectiveness out of the training. So how do we target those people [who click the links]?” AusPost research analyst Deb Fuzy said.
“We can’t improve the training material because they’re not reading it. We could help them better spot the phishing email, but a good number say they already know how to - so why aren’t they putting it into practice?
“One email that doesn’t really result in any repercussions doesn’t encourage them to do anything different.”
Clearly staff were becoming desensitised to the tests, which meant AusPost had to think up new, more engaging ways they could emphasise the risk.
Enter ransomware.
This type of attack is less familiar to recipients but is growing in scale and severity, according to Janik and Fuzy.
The infosec team decided to create their own fake ransomware to get staff's attention and drive home the real, tangible risks that can eventuate if staff are not careful about what they click on.
The custom-built ransomware application used low-level keyboard hooks to capture the keys users would press to try and exit the program, and lock them into the ransomware screen.
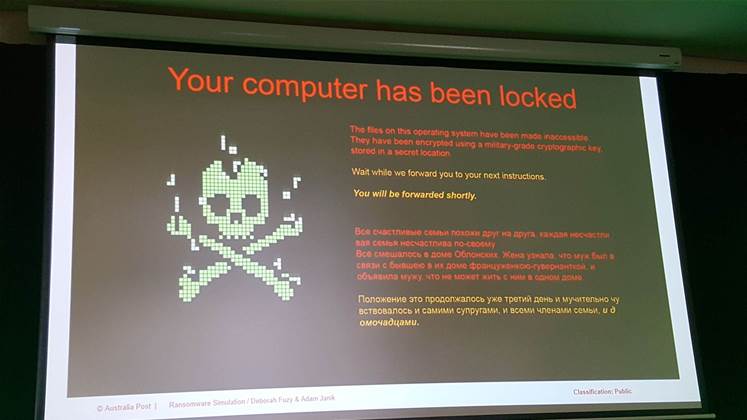
The warning screen itself was designed to be intimidating, coloured in black and red with a skull and crossbones, and Russian translation. It ran for 18 seconds before taking users to training material.
“We figured [18 seconds] was the sweet spot: it’s enough time for people to realise what was going on, read the message that we presented to them, and then think ‘oh crap. I’m in trouble now’,” Fuzy said.
The ransomware was to be launched through a link sent out in a phishing email to around 900 users from across the business.
But given it was the first time the attack vector would be used in an AusPost security awareness campaign, the infosec team decided to test the waters with around a dozen individuals to gauge their response first.
They decided to let end users in on the game: no phishing email was sent, instead an AusPost infosec team member stood alongside the user while they plugged in a provided USB - a Rubber Ducky - and walked them through the process.
What they found was that even with notice of something coming, and a cyber guru standing next to them ready to answer questions, the ransomware simulation was far too frightening for the end user to handle.
Participating users rated their stress levels as a result of the exercise anywhere from six out of five to as high as a 10 out of five.
It stemmed from a lack of awareness about ransomware, the team found.
“The biggest thing they were concerned with was: what do they do when they see this? What do they do to not get ransomware? And what happens if this occurs in their home lives? Half of them had never even heard of ransomware,” Janik said.
The experiment fell too far into the “bad cop” category for the team to forge ahead with their planned full-scale ransomware simulation campaign.
“Stress is a great motivator, but you’ve got to use it very carefully,” Fuzy said.
“It’s really good at helping people learn new things, but you have to make sure you’re doing it to help the employees, rather than to their detriment.
“If we play too much good cop, there’s no real consequences for them to learn from. But if we go straight to bad cop, we can alienate those employees, and if we’re too harsh they’ll start responding very poorly to us in information security."
Not over yet
The team hasn’t given up on a ransomware simulation, however.
The plan now is to educate users about ransomware to get them used to the concept, the same way they became familiar with standard email phishing attempts.
Once the team feels users are comfortable enough with ransomware, they’ll start using the attack vector in their internal campaigns.
“We’re going to continue to try and test it out further with more people, and we’ll explore a few different other ways to get people’s attention - maybe somewhere between the ransomware and the generic training that we’re doing at the moment,” Janik said.
“We know the training we’re running now isn’t quite enough, it isn’t working the way we want it to. We want to see everyone reporting these emails when they come in.”


_(20).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



