Database administrators need to tighten up the security on their installations, with attackers seen abusing weak login credentials to install the "Gh0stCringe" remote access tool (RAT) on them.
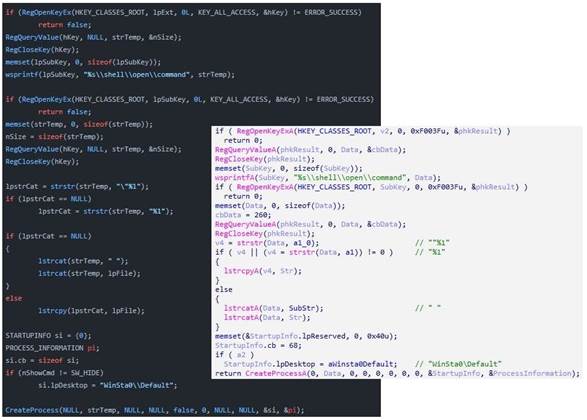
Security vendor AhnLab said Oracle's open source MySQL and Microsoft's SQL Server have been attacked by the malware, which is also known as CirenegRAT and is based on the older Gh0st RAT backdoor.
Gh0stCringe supports multiple commands along with functions that can be enabled after the malware contacts its command and control server, or through settings data during deployment.
Attackers can command Gh0stCringe to download payloads such as cryptominers from C2 servers, connect to specific websites through the Internet Explorer web browser, and also destroy the Master Boot Record (MBR) on the start up disk.
The malware comes with a keylogger that if activated stores user input in the Default.key file in the Windows System directory.
It can also collect Windows system and security product information that is sent on to the C2 server, AhnLab noted.
AhnLab said it's mainly database servers with poorly managed account credentials which are subject to Gh0stCringe attacks, although in some cases unpatched vulnerabilities are also used to deploy the malware.


.png&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



