Microsoft's MSN web portal has been used by unknown attackers to serve up malicious advertising code that attempted to plant the Angler Exploit Kit on visitors' computers.
MSN is the default home page for Microsoft's Internet Explorer browser in its Windows operating system, and the company claims several hundreds of millions of visitors click through to the site every month.
Researcher Jérôme Segura from security firm Malwarebytes reported users were served the malvertising when they simply browsed MSN news, lifestyle or other sections.
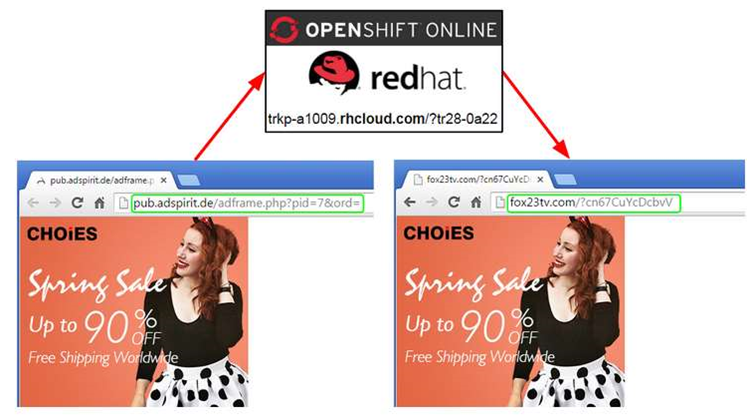
The attackers abused a German network, Adspirit.de, whose ads were served via the AppNexus online advertising delivery company, in order to silently deploy Angler on users' machines.
Segura said the MSN malvertising campaign is the work of the same, unnamed actors that targeted Yahoo recently, as well as a range of other well-known media sites and web properties such as Drudge Report, Weather.com and online marketplace eBay.
Malwarebytes tracked the chain of sites used to deliver the exploit kit, and found the attackers this time leveraged Red Hat's RHCloud cloud platform to perform multiple site redirections to obscure the origin of the infection attempt.
A spokesperson for AppNexus told iTnews it had "deactivated immediately and notified all parties involved".
"AppNexus has a dedicated team of engineers and invests heavily in the scanning of creatives. We take notifications like Malewarebytes' very seriously".
Online advertising has over the past years increasingly been used by internet criminals to spread malware on a large scale, reaching millions of users to infect them en masse.
iTnews has reached out to Microsoft and AppNexus for comment on the incident.


_(36).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



