Microsoft is declining to patch a two-year-old directory traversal vulnerability in all versions of Windows that researchers have labelled a zero-day.
The bug was originally reported to Microsoft in January 2020 by security researcher Imre Rad, and like the recently discovered "Follina" vulnerability it involves attackers abusing Microsoft diagnostic tools to execute malicious code.
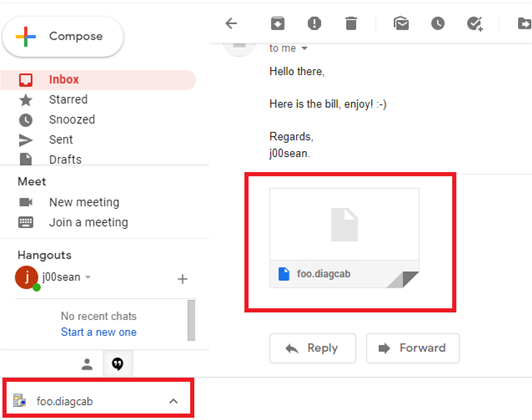
Rad found that a flaw in how cabinet (*.cab) files are verified allows attackers to save the file archives to any location on Windows computers.
By saving a diagcab file to the Startup folder in Windows, attackers can the run their code the next time a user logs in.
Security researcher j00sean rediscovered the vulnerability earlier this month, and noted that it bypasses not only Microsoft Defender, but also browser-based file downloader warnings to users.
Named "Dogwalk" by security researchers, the vulnerability also gets past Microsoft's Mark of the Web (MOTW) security attributes for files that warn users before opening them.
The Spanish security researcher also reported the flaw to Microsoft's security team, but was told the bug doesn't warrant fixing.
Security vendor 0patch has released free micropatches for Dogwalk that adds the missing security check, without a Windows reboot required.
At this stage, it is not known if the Dogwalk zero-day has been actively exploited by attackers.


_(37).jpg&h=140&w=231&c=1&s=0)








 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



