A spate of attacks targeting more than 10,000 unsecured, internet-connected databases around the world has seen a large volume of data deleted and blackmailers demanding a ransom to restore it.
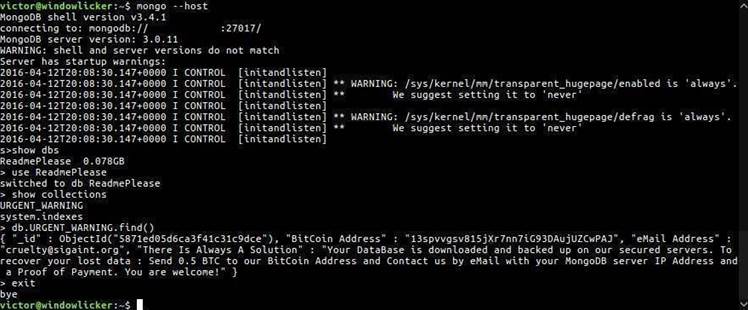
Attackers have honed in on open and unsecured installations of the popular open source MongoDB NoSQL database, replacing the information they once stored with a table containing a ransom note.
Vulnerable MongoDB instances are easily found via scanning services such as Shodan.io. The attack requires very few technical skills, and take just a few seconds to conduct.
In many cases, information in the databases is not backed up, leaving administrators vulnerable to total data loss.
John Matherly who operates Shodan.io estimated the amount of data stored in vulnerable MongoDB instances has reached over 364 terabytes.
Multiple attacks were reported last week and these have continued over the weekend, with researcher Niall Merrigan estimating that up to 10,500 servers have been "ransacked" by at least five different actors, and possibly as many as 12 groups in total.
Merrigan and fellow researcher Victor Gevers are maintaining a spreadsheet on Google Docs of the attacks in which blackmailers ask for ransoms between 0.1 to 1 Bitcoin (A$125 to A$1250 approximately) to restore deleted data.
However, Merrigan advised victims to check their server logs first to see if the data has been exfiltrated before paying the ransom, as evidence suggest attackers don't necessarily save it before deleting databases.
Gevers added that only one in eight attackers actually copy the data over to another host, but researchers aren't sure which group this is.
Andreas Nilsson, director of product security at MongoDB, responded to the attacks with a blog post advising users to secure their databases to avoid falling victim to blackmailers, including enabling authentication on unprotected systems.
Nilsson also published a step-by-step guide on what to do if operators suspect their MongoDB instances have been compromised, and how to restore from a recent backup.
MongoDB instances connected to the internet have been targeted by attackers over the past couple of years, as older versions installed without any form of access authentication enabled could be accessed freely, exposing terabytes of user data.


_(36).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)

.png&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



