Mobile device management (MDM) is a powerful tool for enterprise administrators but concerns are being raised that bad actors could use it to deploy malware onto victims' smartphones.
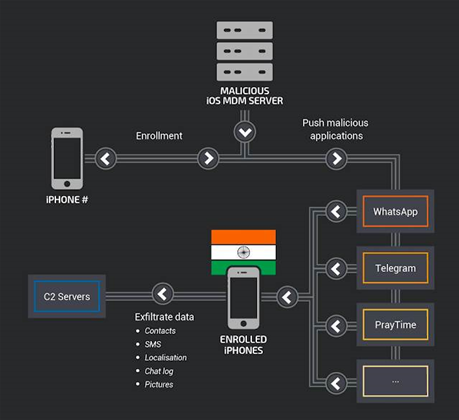
A recent story in Vice quoted Russian infosec vendor Kaspersky researchers having found an "iOS implant" developed by Italian company Negg, which specialises in government spyware.
The malware is said to feature global positioning system (GPS) location tracking and can listen in on device audio.
Although Kaspersky said the malware "was not fully adapted to infect potential victims", the Russian security vendor analysed an earlier spyware made by Negg called Skygofree and was surprised to find that one of its command and control servers was a rogue Apple MDM system.
Does it follow then that MDM could be used to plant malware onto users' iPhones and iPads?
Without wanting to downplay Kaspersky's findings or the reporting about them, iOS security researcher and chief executive of Guardian Mobile Firewall, Will Strafach, explained to iTnews that the devil lies in the technical details.
Strafach said his company regularly watches the development and deployment of different kind of trackers, spyware and malware on mobile devices, which is concerning.
At the same time, it is vital that the details around this are technically accurate in order to allow users to know precisely what the concern is, and what to do, rather than just be worried, Strafach said.
For starters, while MDMs can indeed be used to take full control over user devices and install digital certificates and executable code on them, on iOS they are very noticeable.
"MDMs are tightly controlled on iOS, as Apple appears to have made the good choice to allow Bring-Your-Own-Device style management while still always explicitly asking the user for consent in the user interface prior to app installation and other actions occurring," Strafach explained.
"Additionally, MDM installations are visible in settings by checking under Settings > General” on your device for a Device Management menu, which may be used to remove the MDM install," he added.
"There will also be a notice at the top of the Settings screen if the device is Supervised - a mode used on corporate-owned devices which generally requires a full device wipe to turn on - saying This Device is Supervised and Managed by CompanyName."
Since MDM control of devices is so visible to users, attackers would have to rely on targets never checking their smartphone settings, Strafach said.
He speculated that instead of malware being deployed on average users' devices, Kaspersky might have come across corporate spyware.
Security vendor Zimperium founder Zuk Avraham chimed in and agreed with Strafach that MDMs are unlikely malware deployment vectors.
Afaik, real world attacks do not require MDM. Some require link click, some require being in the same network / physical distance. Others abuse vulns in IMs, baseband or iMessage: (0-1 clicks)... and there are other vectors, which were a surprise to me too TBH. https://t.co/NsMK02lfnS
— Zuk (@ihackbanme) November 27, 2018


_(22).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition











_(1).jpg&h=140&w=231&c=1&s=0)



