Cisco has updated the Google Chrome browser extension for its popular WebEX business web conferencing software after a researcher discovered it could be abused to run arbitrary code remotely on users' computers.
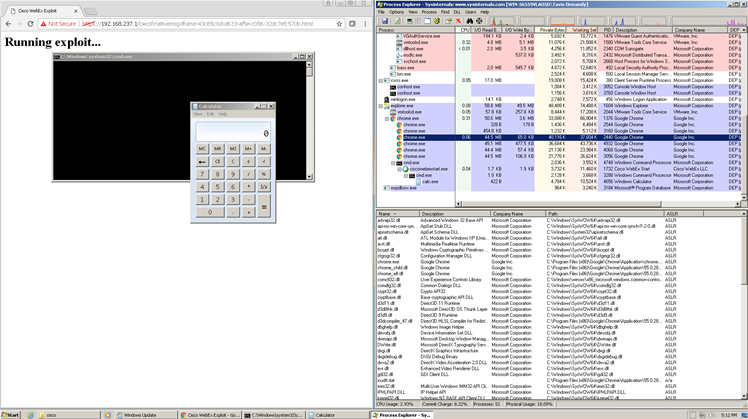
Google Project Zero security researcher Tavis Ormandy analysed the WebEx Chrome extension's behaviour with a meeting running in the browser, and found that it works on any link that contained the
"cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html" pattern.
Ormandy was able to code a proof of concept exploit that made the WebEx Chrome extension pop up the Windows calc.exe application.
He noted that as the magic pattern can be embedded in HTML inline frames, "there is not necessarily any user-visible indication of what is happening, visiting any website would be enough".
Cisco responded quickly to Ormandy's bug report, and over the weekend released the fixed version 1.0.3 of the WebEx Chrome extension.
The fix limits the magic URL to *.webex.com and *.webex.com.cn domains, which means a user must click OK for remote code execution to occur.
Ormandy noted that the fix "does mean any XSS [cross-site scripting] on webex.com would allow remote code execution", but said if Cisco feels that that is an acceptable risk, the patch is adequate.
Cisco's WebEx extension for Google has around 20 million active users, Ormandy noted.
Update 25/1/17: Despite describing Cisco's patch as acceptable, Ormandy today revealed there were further remote code execution bugs in WebEX that need to be fixed.
The details of the vulnerabilities were not disclosed by Ormandy, pending a fix by Cisco.
There are some remaining remote code execution problems with the WebEx 1.0.5 update. I've just sent a full report & exploit to Cisco. ⚠️��
— Tavis Ormandy (@taviso) January 25, 2017


_(23).jpg&h=140&w=231&c=1&s=0)

_(33).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



