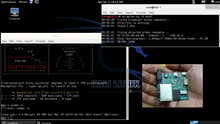
A computer small enough to fit inside the palm of a hand sits in the corner of an office, its lights blinking. It looks like a toy to most, but the small ARM-based machine is running the latest version of Backtrack, and is breaking into the corporate network.
Such a feat was not supported out of the box prior to this evening's release of Kali, the sixth installment of the uber-powerful and super-secure penetration testing platform.
BackTrack obtained official support for ARM-based devices as part of its quiet year-long and ground-up overhaul by the small group of security professionals who designed the operating system, now considered essential kit for penetration tests.
The authors hailing from Offensive Security together with security professionals at Rapid7, who offered free assistance in the rebuild, announced Kali at BlackHat Europe.
Outwardly, Kali looks the same as the previous version of BackTrack. But dig a little deeper, according to founder Mati Aharoni, and that's where the similarities end.
"It boots like BackTrack, but when you look deeper into Kali, you see all these amazing new features that just weren't available in BackTrack," Aharoni told SC speaking ahead of the launch in Amsterdam.
"Everything has changed."
Kali has become sleeker and more secure: All packages were subject to a vetting process and were signed by developers with GPG keys.
This Aharoni said introduced complete visibility into the development chain.
"There is a very clear public development of each package so you can see changes easily. Visibility increased ten-fold."
The Metasploit Framework too has been rebuilt. Rapid7, keen to remove the rough-around-the-edges integration of the popular exploit arsenal within BackTrack, contacted Offensive Security. In a streak of luck, the call came in early in Kali's development.
From there, Metasploit underwent a considerable overhaul to become one of the most complex packages in Kali.
"Users will be in for a much smoother ride," Aharoni said. "It was never built to be packaged as a distribution so we needed to massage it"
This took the form of a Debian repo rather than an at times messy binary installer, Rapid7 product manager Christian Kirsch said.
"A tonne of our users were using Metasploit on BackTrack," Kirsch said. "Now if you update Kali, you update Metasploit."
"It is critical to take the view of the attacker to see if your defences are working. The smartest people in the world may make mistakes in setting up defences."
It is also features a more friendly user interface and was available in the paid professional edition.
A razor has been applied to BackTrack's pre-packaged pen testing tools, eradicating 50 unpopular tools and introducing more powerful offerings into Kali.
iKat, a hacking tool to audit the security of browser controlled enviroments like Kiosks, Citrix Terminals and WebTVs, was one such addition. The developers went to lengths to get the tool on board and had even helped the author further develop and integrate it into Kali.
Kali comes as fully customisable. Users were able to pick and choose the tools they want in the platform, including private applications, prior to downloading the ISO, even down to their choice of wallpaper.
This Aharoni said makes Kali open to low-end systems and ARM based devices. Pre-built packages exist for a host of ARM devices including Raspberry Pi and ODROID.
Kali is now available for download and the wiki page is also online.
Updated with download links.






_(37).jpg&h=140&w=231&c=1&s=0)


_(33).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



