The Australian government's cyber security centre has issued a high status alert to warn users of Atlassian's Confluence that the corporate wiki software contains a serious vulnerability that allows attackers to execute code remotely, with no authentication required.
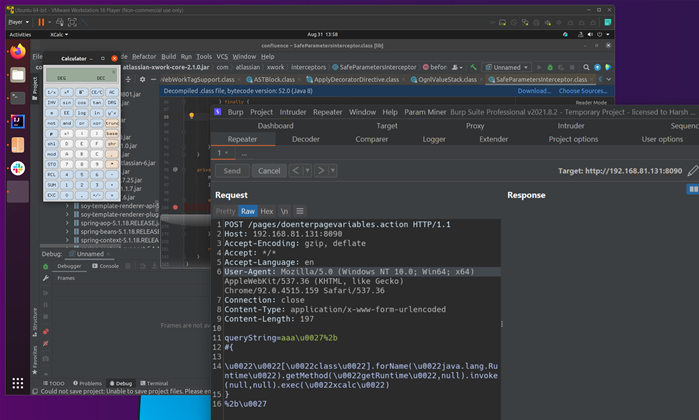
Atlassian said the bug is an Object-Graph Navigation Language (OGNL) code injection vulnerability, affecting self-hosted Confluence Server and Data Centre versions, but not the Cloud variant.
Proof-of-concept code has been published for the flaw, which was discovered by security researcher Benny Jacob.
ACSC and security researchers are warning that attackers are looking for, and attempting to exploit, vulnerable Confluence instances currently.
We've detected mass scanning and exploit activity from hosts in ���� ���� ���� �������� ���� ���� targeting Atlassian Confluence servers vulnerable to remote code execution (https://t.co/GExSx8puLm).
— Bad Packets (@bad_packets) September 1, 2021
Query our API for "tags=CVE-2021-26084" for full payload and source IPs. #threatintel
"Australian organisations who self-host Atlassian Confluence should identify any internet-facing instances of Confluence as a priority," ACSC said.
"Internal instances of Confluence should also be identified."
Confluence customers are advised to upgrade to versions 6.13.23, 7.11.6, 7.12.5, 7.13 or 7.4.11 in which the vulnerability is patched.

.png&h=140&w=231&c=1&s=0)



.png&w=100&c=1&s=0)
_page-0001.jpg&w=100&c=1&s=0)
.png&w=100&c=1&s=0)


.png&w=120&c=1&s=0) Tech in Gov 2025
Tech in Gov 2025
 Forrester's Technology & Innovation Summit APAC 2025
Forrester's Technology & Innovation Summit APAC 2025
.png&w=120&c=1&s=0) Security Exhibition & Conference 2025
Security Exhibition & Conference 2025
 Integrate Expo 2025
Integrate Expo 2025
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition










.jpg&h=140&w=231&c=1&s=0)



