This is a very serious service/application that we have to admit also is very cool. This is an intrusion detection system (IDS)/intrusion prevention system (IPS) on steroids. It uses just about every security paradigm that we can think of. It is tied into a network of honeypots all over the world. It allows both IDS and IPS, and it has a level of detail and drilldown that enables solid forensic analysis of events.
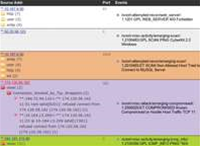
Especially impressive is the service's ability to detect bots and prevent their activities. This capability comes from sophisticated behavior analysis, which can be built into your sensors. The sensors can contain a wide variety of standard and non-standard tools. The commonality, though, is that these tools gather information and then ship it out. That means that users can employ fairly lightweight sensors or, in a sensitive, high performance network opt for far higher performance sensors. The choice is up to the user. However one goes, though, the sophisticated analysis and correlation is performed in the cloud, a performance and functionality benefit.
Pricing on this service is almost a giveaway - with a starting point of $1,089 per year for a single core sensor. Depending on what is needed in one's application, 64 cores can be implemented, at added cost, of course. But make no mistake: This may have a lightweight price and a lightweight presence on a network, but what it does is far from lightweight.



_(37).jpg&h=140&w=231&c=1&s=0)

_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



