A new zero-day vulnerability in Adobe's popular Flash media player is being abused by attackers targeting employees in government departments around the world, according to security researchers.
Infosec vendor Trend Micro said the campaign comprised of spear-phishing emails sent to ministries of foreign affairs with links that purported to lead to current affairs events information.
Instead, the links lead to sites hosting malicious exploit code.
Spear-phishing emails using the below topics have been collected by Trend Micro:
- “Suicide car bomb targets NATO troop convoy Kabul”
- “Syrian troops make gains as Putin defends air strikes”
- “Israel launches airstrikes on targets in Gaza”
- “Russia warns of response to reported US nuke buildup in Turkey, Europe”
- “US military reports 75 US-trained rebels return Syria”
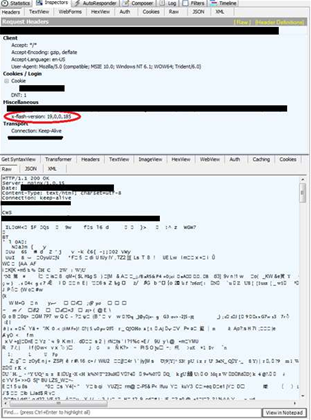
Trend Micro identified the Pawn Storm group as the culprits behind the campaign, which hones in on a vulnerability in Adobe Flash version 19.0.0.185 and 19.0.0.207.
They said the flaw could also affect earlier versions of the media player.
Pawn Storm was believed to be responsible for an earlier malware attack using a zero-day in Oracle's Java application framework in April this year.
That campaign was directed at members of the North Atlantic Treaty Organisation (NATO) military pact, as well as the United States government.
Adobe has been notified of the issue by Trend Micro, the firm said, with the two companies working on addressing the zero-day.
The Flash player has a history of critical, exploitable vulnerabilities going back many years, with several sites such as Google YouTube moving to HTML5 to replace the Adobe software.

.png&h=140&w=231&c=1&s=0)





_page-0001.jpg&w=100&c=1&s=0)

 Government Innovation Showcase Queensland
Government Innovation Showcase Queensland
 Government Cyber Security Showcase Queensland
Government Cyber Security Showcase Queensland
 Local Government Focus Day Queensland
Local Government Focus Day Queensland
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition
 iTnews Benchmark Security Awards 2025
iTnews Benchmark Security Awards 2025











.jpg&h=140&w=231&c=1&s=0)



