Firewall vendor FortiNet has denied that the FortiGate OS operating system that runs its devices comes with a backdoor, despite a researcher purportedly posting proof of concept code on a security mailing list.
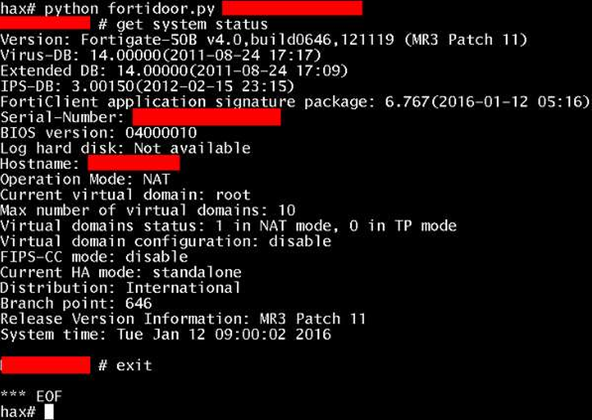
Over the weekend, a Python script was posted anonymously, which appeared to allow remote access to Fortinet devices over the Secure Shell protocol. The post disclosed a passord hard-coded into the FortiGate OS.
The password is said to work on FortiOS version 4.x to 5.0.7, and a screenshot was posted on Twitter, allegedly showing that the script for the backdoor is working, providing remote access to Fortinet devices.
However, the vendor issued a statement denying the vulnerability is found in any versions of its firewall operating system released after July 2014.
"The recent issue that was disclosed publicly was resolved and a patch was made available in July 2014 as part of Fortinet’s commitment to ensuring the quality and integrity of our codebase.
"This was not a 'backdoor' vulnerability issue but rather a management authentication issue. The issue was identified by our product security team as part of their regular review and testing efforts," the company statement said.
An investigation into the vulnerability by Fortinet showed there was no malicious activity, but the company did not specify why the hardcoded password was included.
FortiGate OS versions 4.3.17, 5.0.8, 5.2 and 5.4 or later are not vulnerable, the company said, and encouraged users to upgrade to newer operating system versions immediately.
Just before Christmas last year, competing firewall vendor Juniper discovered a backdoor in its Netscreen devices, and issued an urgent alert to customers to patch these as soon as possible.
The backdoor in Juniper firewalls allowed for the silent interception of traffic, and has been around since 2012.
While Juniper did not say who it suspected was behind the sophistcated backdoor, security researchers believe it was introduced by the United States National Security Agency (NSA), exploiting a deliberate weakness in a cryptographic algorithm planted by the government intelligence bureau.


.png&h=140&w=231&c=1&s=0)

.png&h=140&w=231&c=1&s=0)





.png&w=120&c=1&s=0) Tech in Gov 2025
Tech in Gov 2025
 Forrester's Technology & Innovation Summit APAC 2025
Forrester's Technology & Innovation Summit APAC 2025
.png&w=120&c=1&s=0) Security Exhibition & Conference 2025
Security Exhibition & Conference 2025
 Integrate Expo 2025
Integrate Expo 2025
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition




.jpg&h=271&w=480&c=1&s=1)






.jpg&h=140&w=231&c=1&s=0)



