Dell has been caught out installing a bogus X.509 digital certificates for SSL/TLS security connections on its computers, putting users at risk of man-in-the-middle interception attacks.
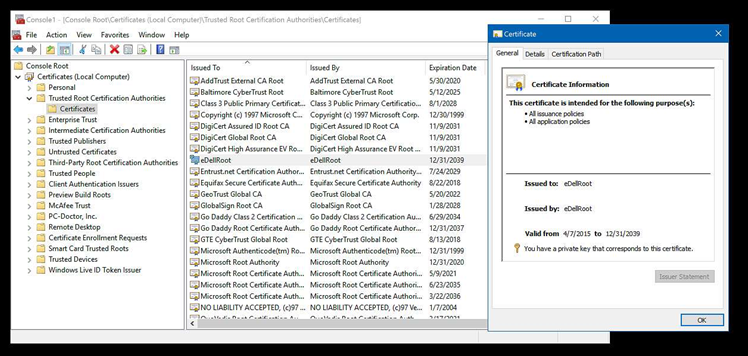
Kevin Hicks detailed his findings on internet forum Reddit's /r/technology group, saying he discovered that a new Dell XPS 15 laptop comes with both a self-signed root certificate authority (CA), and a private key for it, preloaded.
The circumstances echo that suffered by competing PC vendor Lenovo, which caused a stir earlier this year when it was caught shipping computers loaded with the Superfish adware.
Before Hicks' discovery, Citrix program manager Joe Nord also noted the bogus CA. The certificate and its private key on Nord's machine are the same as on Hicks' system. Other users investigated their machines and also found the same CA and private key.
The CA is valid until 2039, and is difficult to remove from systems without technical expertise.
Although the private key for the eDellroot CA was marked as non-exportable, Hicks was able to extract it with a software utility.
Hicks was also able to use the Dell CA to sign fake server certificates that could be used to trick users into thinking an attacker's website is authentic, as well as signing potentially malicious applications.
Dell support confirmed via Twitter that the CA is installed on its machines when asked by Hicks.
"It's a Dell trusted certificate that is mentioned in the OS. It doesn't cause any threat to the system, so we don't recommend you to edit the registry. Let me know if there is anything else I can help you with," a Dell support staffer told Hicks.
Dell said it is investigating the reports of fake CAs.
The company did not reveal why it installed self-signed root CAs with the same private key on its machines. It's referenced by a Dell dynamic link library (DLL) file that forms part of the company's preloaded software suite.
In February this year, Lenovo had to urgently issue a security alert and release tools to clean users' machine of Superfish adware that also installed a fake root CA that would sign digital certificates that were then trusted by web browsers.
Lenovo initially denied there was a risk to users, but had to back down in the face of worldwide furore, and the United States Computer Emergency Readiness Team warning that the company's consumer PCs were vulnerable to HTTPS spoofing thanks to the Superfish adware.
Update:
"The recent situation raised is related to an on-the-box support certificate intended to provide a better, faster and easier customer support experience," Dell said in a statement.
"Unfortunately, the certificate introduced an unintended security vulnerability."



.png&h=140&w=231&c=1&s=0)





 Okta Identity Summit
Okta Identity Summit
.png&w=120&c=1&s=0) Security Exhibition & Conference 2025
Security Exhibition & Conference 2025
 Integrate Expo 2025
Integrate Expo 2025
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition
 iTnews Benchmark Security Awards 2025
iTnews Benchmark Security Awards 2025











.jpg&h=140&w=231&c=1&s=0)



