Keys, wallet, smartphone, laptop thumbdrive of sensitive corporate secrets: this is the list the average businessperson runs through before leaving the office.
But if a Ponemon Institute study this month of 967 respondents is to be believed, more than two in five have lost a device such as a USB drive that held data.
Memory product maker Kingston Technology released the first 128GB thumbdrive ($700) last week, which holds nearly 200 films, 44,000 songs or 27 million text files. That's a lot of corporate secrets to trust to such a package so flimsy on security.
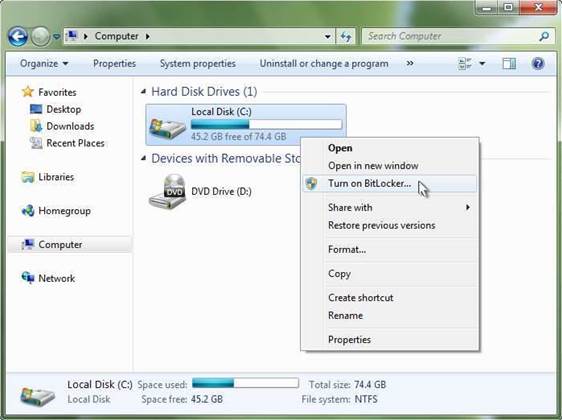
BitLocker To Go, a key feature Microsoft's latest operating system Windows 7 to be released on October 22, is entering a field dominated by the likes of IronKey and Trend Micro to protect data stored on these tiny devices.
At a reviewers' briefing yesterday in Sydney, Microsoft Australia IT Pro evangelist Jeff Alexander demonstrated how the security software that comes with the next Windows halts data walking out the door.
Group policies are set so that information can't be written to a device such as a thumbdrive unless it was first encrypted with BitLocker To Go. Legacy desktops running Windows XP, for instance, read data stored on the devices using software that is installed when the BitLocker partition is created.
Deployment is simplified for IT managers because BitLocker doesn't need to be set up when the OS is installed. Chief information security officers can make a stronger case to deploy Windows 7 because group policies control its use under Windows Server 2008 R2.
Key escrow is held in Active Directory, easing recovery of lost passwords. And users benefit because the encrypted thumbdrives may be set to open on PCs they use routinely without entering passcodes, Alexander said.
Multi-factor authentication through the use of smart cards or biometrics may be deployed to strengthen access to corporate data.
AppLocker, another new feature, gives administrators fine control over which applications to allow on their fleet PCs. Prohibited applications are determined by rules such as program name, author or its unique signature (called a "hash tag") that will survive software updates.
Although Windows 7 built on the security foundations of Vista that it replaces, Microsoft flagged that some "low-level" applications such as firewalls and anti-virus software may need to be upgraded.
System administrators and helpdesk staff should find troubleshooting user problems is eased through the Problem Step Recorder that emails pedagogic screenshots and a text file illuminating the steps a user takes before they hit an error.
Windows 7 is netbook friendly, Microsoft said, and the Home Premium version will have the same installed "footprint" as its bigger brothers. Every version of Windows 7 (except the basic "Starter" pack) has identical features that are activated using the Windows Anytime upgrade function. Administrators buy activation keys to upgrade their installation although Microsoft was unsure about whether they would get these from the software maker or a reseller.
Microsoft also demonstrated an operating system "refresh", which erased an existing installation of Windows XP or Vista to replace it with Windows 7. It copied 6.3GB over 541 files of user data in about half an hour.
To follow Australian reviewers' comments during the session, search #W7AU on Twitter.
Key security features
BitLocker (improved from Vista SP1)
- Minimum partition size 100MB
- Simplifies encryption and key management for all drives using the Data Recovery Agent.
- Store recovery information in Active Directory.
- Right-click on drive in Explorer to enable.
- Hidden partition created on Windows installation (no need to repartition the drive later).
BitLocker To Go (new)
- Protects data on removable drives.
- Option to require BitLocker To Go to store data on removable drives.
- Reader installed on partition to access encrypted drives on earlier Windows versions (no OS X support).
AppLocker (new and improved)
- Admins set fine rules for which applications are permitted that survives software upgrades.
- PowerShell "cmdlets" when used with the audit function test and automate policies controlling software deployment on PCs.
- Custom error messages may be set to inform the user when they attempt to access a prohibited application.


.png&h=140&w=231&c=1&s=0)


_(20).jpg&h=140&w=231&c=1&s=0)



_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition











_(1).jpg&h=140&w=231&c=1&s=0)



