Using Endpoint DLP (data leakage prevention), administrators have a vast amount of access control over peripheral ports, removable media devices, as well as network and application protocols. This ensures that only authorized devices, such as USB flash drives, microSD cards and other types of media, are used in the network and only authorized users can use said devices preventing data leakage and other compliance problems.
Installation and deployment was quite straightforward. The initial implementation was comprised of installing the enterprise server somewhere in the environment. The server software itself was lightweight and installed on pretty much any machine. Once the server was installed, the DeviceLock service was deployed quickly to client machines either through Active Directory Group Policy or by using the Endpoint DLP management console. With the service deployed, all endpoints throughout the enterprise were managed natively using Active Directory Group Policy.
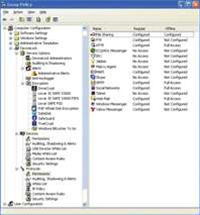
The Endpoint DLP Suite features a native Active Directory Group Policy Microsoft Management Console snap-in, so administrators can modify policy and configure options using the existing group and organization unit structure already in place. The snap-in itself provides a lot of configurable options including port management, encryption requirements, application protocol controls and auditing options. We found this product to be quite simple to manage and configure overall. We really liked the approach of tying policy directly to Active Directory for added ease of use and management.
Documentation included a quick-installation guide, as well as a full administrator manual. The short quick-installation guide provided a brief overview of the suite's components and how they are deployed, while the administrator manual provided full in-depth instructions on installation, deployment, configuration and management of the product. We found the administrator manual to be well-organized with easy-to-follow, step-by-step instructions and a lot of screen shots, diagrams and configuration examples.
DeviceLock offers customers the first year of support as part of the initial cost of the product. After the first year, customers can purchase additional assistance as part of a contract. Support offered by DeviceLock includes eight-hours-a-day/five-days-a-week phone-based technical help and 24/7 email and web-based aid. Customers can access a large web-based area, which includes many resources, such as a FAQ section, user forum, support ticket request form, webinars, video demos and product documentation.
At a volume discount price of $40/perpetual license per seat for 1,000-plus endpoints, this product may seem a little on the expensive side, but we find it to be an excellent value for the money. The DeviceLock Endpoint DLP Suite comes complete with a lot of configurable options and a great amount of flexibility and control that make it simple to deploy, configure and manage. The added ease of management through Active Directory alone makes this product easy to deploy in almost any environment with little effort from administrators.
Very strong offering with a good DLP feature set. We make this our Recommended product.


_(23).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



