FireEye has denied that it asked a fellow security vendor to fire a researcher that had publicly disclosed vulnerabilities found in one of its key products during a security challenge.

On Tuesday Australian time, reseacher Jean-Marie Bourbon of French IT vendor Sogeti posted details of multiple vulnerabilities in security firm FireEye's Malware Analysis System 6.4.1, along with proof-of-concepts exploits for them.
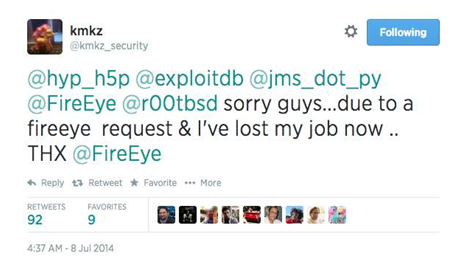
Soon afterwards, Bourbon took to Twitter to announce that he'd been fired from Sogeti, on behest of FireEye:
Dan Wire, FireEye's director of communications, denied the charge in a conversation with iTnews.
"As a matter of policy, we take vulnerabilities very seriously - but not personally," he said. "We've asked all parties involved to follow responsible disclosure as is standard in the security industry so we can keep our customers safe.
"We didn't ask that anyone was sacked," Wire said.
Sogeti did not respond to a request from comment from iTnews.
Bourbon later told Forbes Magazine that he had been suspended, rather than fired, but insisted that FireEye had put pressure on Sogeti to punish him.
The vulnerabilities discovered by Bourbon include three cross-scripting flaws, one cross-site request forgery hole, file and path disclosure in MAS 6.4.1 and SQL database injection issues.
Bourbon told Forbes that he had found the flaws on his own time, outside of Sogeti, and that he notified FireEye about these in May. FireEye has requested that the postings on the vulnerabilities on security forums be removed, but they can be found elsewhere easily.
FireEye has released a security bulletin [PDF] for the vulnerabilities and that many of them had been communicated in product release notes.





_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



