Social engineering threats like Trojan Horse malware are on the increase as exploitable vulnerabilities in software decline, according to Microsoft's latest security report [PDF].

In the last six months of 2013, infection telemetry data sent by Microsoft antimalware products showed that consumers are more than twice as likely to encounter malware than better protected enterprise users.
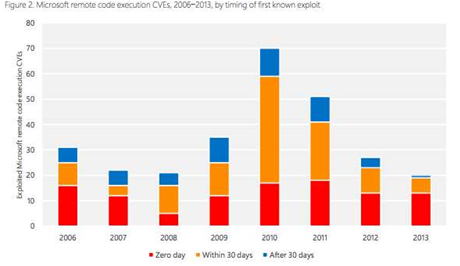
Microsoft gives itself a pat on the back in the report, claiming that its Computer Security Science team's research showed a 70 percent drop in remotely exploitable vulnerabilities in its software between 2010 and 2013, even though the number of zero-day holes rose last year.
Despite fewer remote exploits, the number of computers that had to be "disinfected" more than tripled in the last quarter of 2013 as deceptive and ransomware downloads rose.
Such downloads were the top threat in 95 per cent of the 110 countries and regions studied in the Microsoft Security Intelligence report, as attackers bundled malware into seemingly innocuous content such as music files, games and other software.
The most common category of malware that Microsoft's security team saw in the last quarter of 2013 was Trojan downloads and droppers like Win32/Rotbrow, along with miscellaneous Trojan Horses such as Win32/Obfuscator.
Rogue security software or scareware is also a problem, with users being tricked into downloading programs to remove non-existent threats and in doing so infecting their computers with malware.
Ransomware such as Reveton and CryptoLocker that locks users out of their computers until they pay the blackmailing attacker to unlock it also earns a mention in the Security Intelligence Report, targeting users in not just wealthier English-speaking countries but also Russia and Asia.
According to Microsoft data, the ransomware threat increased by 45 per cent globally in 2013, as attackers found it an easy way to "make a quick buck."



_(20).jpg&h=140&w=231&c=1&s=0)
_(22).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition











_(1).jpg&h=140&w=231&c=1&s=0)



